Building Industrial IoT with IOTA: Introduction and How IOTA Works
Blockchain is making a loud, impactful noise on the digital front of our world. And, we are accepting it.
Because of blockchain, we are trying to make things that we otherwise could have never ever imagined. Things like:
- Smart contracts
- Smart home and cryptographically mapped relationships
- New rental models
- New servicing models
The list of fortune 500 getting into blockchain is getting huge day by day. It can be said that Blockchain is one of the most revolutionary technologies of 2019 that can be used in software product development.
Starting this year, we started to build on blockchain and it’s business potential bits-by-bits. The absolute opportunity to run a distributed trust network was extremely revolutionary for us.
But, as we worked and tested one service to another, we found that many of these blockchain services lacked scalability. The scalability challenges were further enhanced by high costs per second and the lack of transparency involved in these networks.
This is when we were introduced to IOTA.

Architecture of IOTA
In traditional blockchain models, transactions are bundled in each block after getting verified by the miners. So, as the number of transactions increases, the work for miners increases as well.
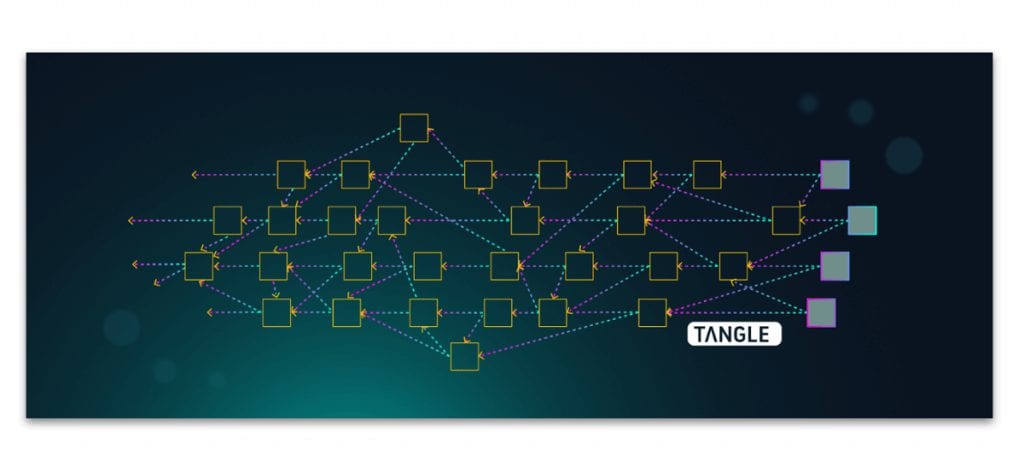
In IOTA, instead of a global blockchain, we have directed acyclic graph, called Tangle. This Tangle graph is the ledger for storing history of all transactions.
As opposed to that, in a Tangle architecture each transaction will form a new block and will be verified by itself. In order to carry out this verification, it needs two randomly chosen transactions in the same network.
IOTA’s is decentralized and is indefinitely scalable with zero cause, allowing us to build a self sustainable economy on-demand. Perfectly fitting the next generation business models.
How does IOTA works?
IOTA has nodes. A node is a part of the global IOTA network and is constantly exchanging information with its neighbours. This information is the status of the network: who made transactions, how many transactions were made, etc
Your node’s IP has to be static in order for it to stay connected with the tangle. Otherwise, your neighbours will have to keep updating your IP everytime it changes.
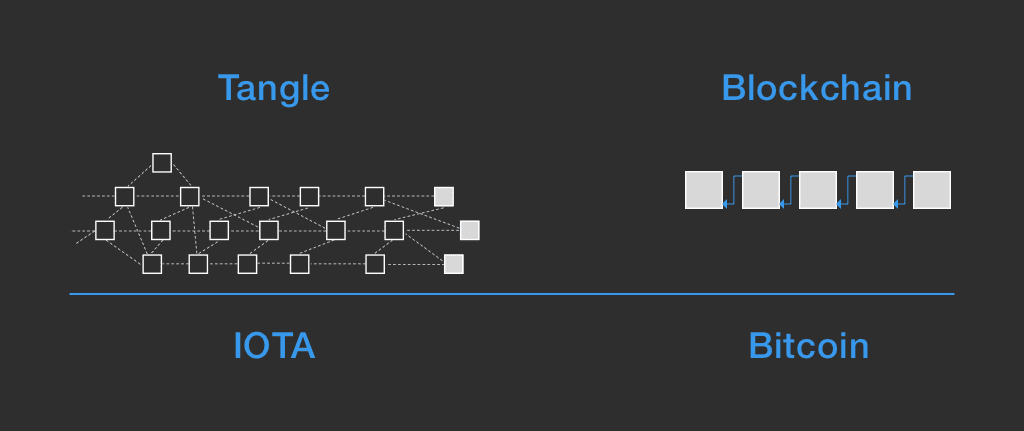
How IOTA is different from blockchain?
The cryptocurrency IOTA itself doesn’t runs over blockchain, and runs on top of their own ledger called Tangle. It is said to be immune towards quantum computers. In case, if quantum computing is made possible, IOTA would be one of the very few IoT solutions available that will be secure.
IOTA is a quantum resistant Directed Acyclic Graph(DAG)
When it comes to cryptography and encryption, quantum computing can seamless break them down. Making any encryption layer a false hope for protecting our mission critical IoT systems. Tangle network is the hope for our secure future, whereas the entire existing of crypto-algorithms is extremely doubtful.
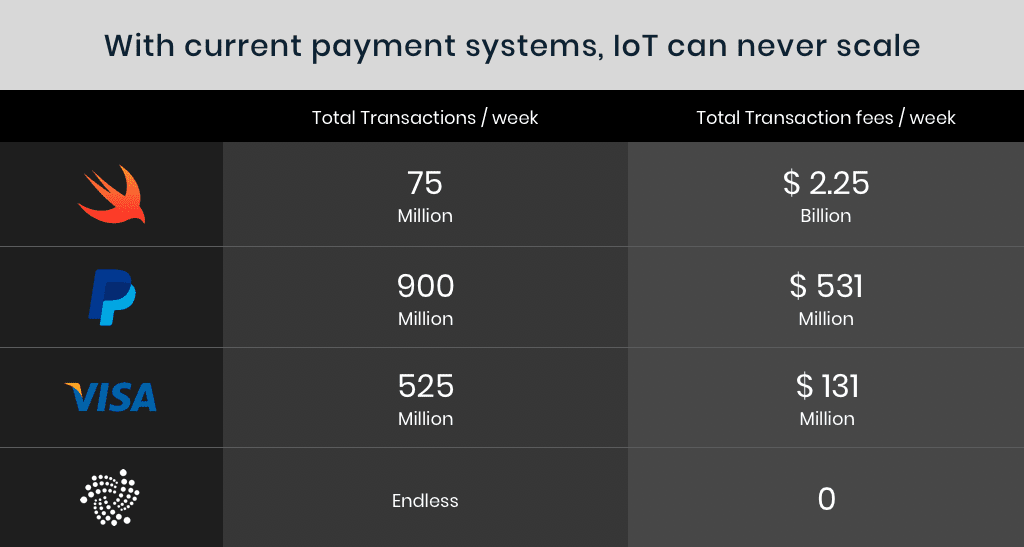
When it comes to future of IoT, we see millions of transactions, let me rephrase it – microtransactions. Getting slowly into the needs of real time transactions, most available blockchain solutions wouldn’t scale as they won’t be able to scale to a higher number of transactions per seconds and at the same time provide stable infrastructure and run on a lightweight hardware.
Now add a transaction fees to these millions of microseconds, that’s just the scalability killer!
In IOTA, tokens are never lost: No miners involved
In other solutions that involve blockchains, the presence of miner requires IoT networks to be fed consistently with more cryptocurrencies. A miner will keep consuming cryptocurrencies, and hence arises the need to manage and purchase more cryptocurrency makes building future IoT networks difficult.
In IOTA however, there are no miners present. And, any IOTA that has been exchanged, can always be sent back. This makes is extremely cost efficient to just keep moving IOTAs back and forth into an IoT network, eliminating the need to purchase more IOTAs for a very limited number of devices.
The illustration below shows the difference:

How IOTA protects against spamming or DoS attacks?
In traditional blockchains, it brings a lot of chances for an attacker to carry out a 51%(in reality only a 34%) attack. And the only requirement to carry out this attack would be to have that percentage of network hashing rate.
Now, IOTA’s network topology and protocols are way different from most blockchains, and percentage of hashing rate is one of the many factors
Use of Coordinators to safeguard against attacks
Coordinators in IOTA are essentially training wheels for the IOTA network till the amount of organic activity on the ledger is sufficient to where it can evolve without any further assistance. When that happens, coordinators will be completely shut down.
The hardware requirements (MCU) for IOTA?
In order to run an embedded IOTA node, the minimum hardware requirements:
- Weak devices should use the swarm technique
- For other SBCs, an architecture better than i386 would work
IOTA isn’t divisible
IOTA isn’t divisible, all decimals have been removed to create large quantities. Currently, there are 2.7 quadrillion IOTA making the issue of non-splitting cryptocurrency not a big problem.
The problem with non-splitting IOTA isn’t a really big concern as a node would split in a very similar way any two parties would split a $57 bill at a restaurant.
Why a transaction points to 2 transactions? Why not 3/4/5 transactions?
As IOTA Tangle evolves, the width varies depending upon on certain parameters of its environment like network topology. The parameter’s value fluctuates and Tangle width reacts to that trying to maximize the performance. Pointing towards two transactions brings protection against a malicious user who might try to affect the width to reduce overall performance.
If there were three, four, or five transactions, an attacker would gain an advantage.
Myth: IOTA and it’s security dependencies on number of transactions?
Many are casually assuming that in IOTA, the security is proportional to the number of transactions. And, if an attacker wants to double their spend after 1 hour since his transaction, he needs to submit number of transaction for the last hour of his transactions to invalidate his first spend.
Truth: IOTA’s security is multiplied by a quotient depending on network topology. The above only applies if there were no latency between network nodes.
What happens when a Tangle is split into two pieces?
It is quite possible that with IOTA gaining huge traction, big mesh networks – on a global scale would be created. Let’s say if this huge mesh network is split into two or three sub nets.
In any other blockchain solution it would be easy for them to converge once the connection is re-established. But in IOTA, they won’t be able to converge fully without a lot of reattachments.
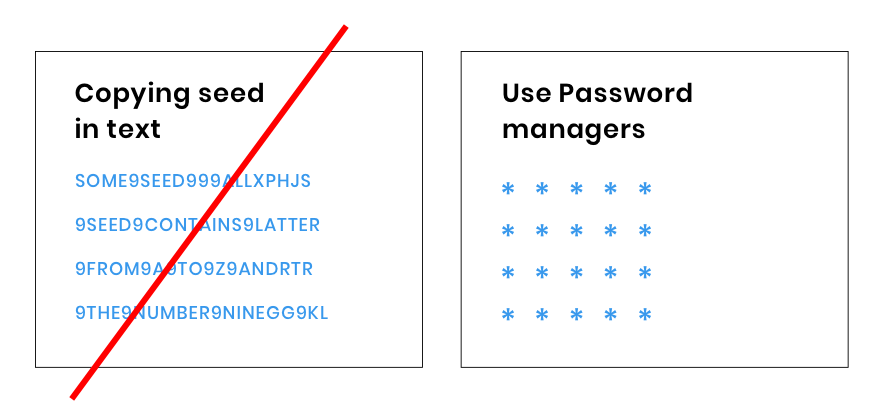
A security hole in the $1 billion cryptocurrency market?
The current usage model of IOTA requires typing the seed in plain text. It seems like a huge security hole in implementing IOTA. There are password managers that can use copy and paste obfuscation.
When you integrate IOTA with your platform, you can integrate these password managers with the system to make the seed encrypted and the problem of plain text goes away.
Making IOTA even more secure
There has been talks about IOTA being vulnerable to hashrate attacks, and working independent of Coordinator has been extremely confusing to many.
With IOTA things are more customizable, you can for example use a maximum acceptable transaction frequency derived from an upper quantile of a distribution of transaction frequencies. Introducing throttling, a “dynamic throttling” within tangle protocol at the node level with probabilistic approaches would create a dynamic governor that would take care of coordinator’s role in IOTA.
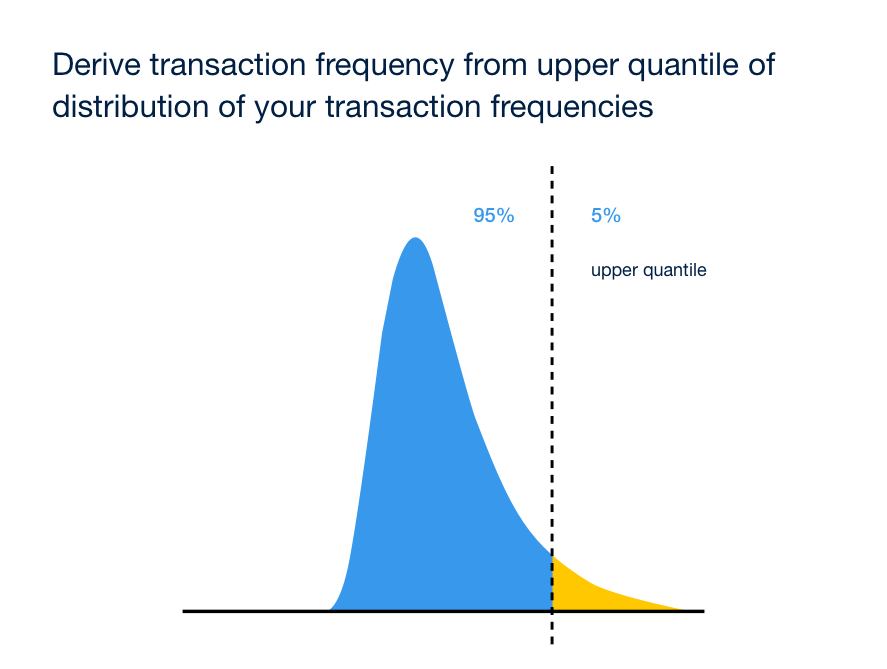
Using distributions, which uses dynamic values, this governor logic would be able to safely scale and improve confirmation times, bringing zero risk of 34% attack immediately.
Upon implementing the governor’s logic, an attacker would have to build up an attack for weeks, and the actual nodes will follow attacker’s frequency till they are their maximum capacity.
So far the governor’s logic only delays the attacker, reducing his ability to immediately attack the IoT network.
A better solution – Bankrupt the attacker
You can impose a tiny transaction fee to that should be paid to nodes whenever the transaction frequency exceeds a threshold setup up by the developers within each node software update. An attacker would try to keep increasing his transaction frequency until every other node gives up – This is the sole way to perform an attack.
But, as we have incurred a transaction fee whenever the transaction frequency is exceeded, this would eventually bankrupt the attacker.
Making each attack on your IoT networks decreases the incentives to attack.
Preventing someone from becoming omnipresent
IOTA doesn’t use automatic peer discovery, this has been done to increase security within IoT mesh-nets. Bringing manual neighbour tethering allows to prevent someone from becoming omnipresent.
Selfish strategy over IOTA
When we talk about IoT sensor networks, there are greater things to be remained concerned about; for example, having an equilibrium around large participants charging “transactions” fees to smaller participants for inclusion.
A concern with blockchain networks is that the selfish strategy will reach a point where confirmation isn’t possible because there are too many isolated sub tangles that aren’t merging regularly.
Now, these orphaned sub tangles would only be able to merge back into the main tangle by paying computationally expensive powerful actors to confirm them.
In IOTA however, we saw results simulated on a 20 cluster tangle where transactions were picked randomly and they showed that most of the transactions were still confirmed.
Parent selection strategy
We haven’t seen a parent selection strategy with Tangle yet, but it would be interesting to implement this to make IoT sensor networks even more secure.
LoRa and IOTA
So, when it comes to building a secure IoT network, most decision makers are afraid of bad devices selecting their own transactions as parents. This would increase the chances that someone would pick the bad devices as their parent using one of the random selection strategies.
To effectively tackle this situation, IOTA assumes that when it comes to computing power, 67% of participants would be not self interested and instead are an altruistic participants to some degree.
For those who come from a cloud or a “non-network restrained” environment, this would appear counter intuitive. Mainly because in cloud driven devices, computing power can be increased on demand. Here’s the case study of one of our clients, Freewire, for whom we have created cloud driven mobile and web apps.
When we talk about IoT and the various models involved, it is more about the network. The case becomes extremely clear when we talk about Lora networks, where IoT devices dominate the network.
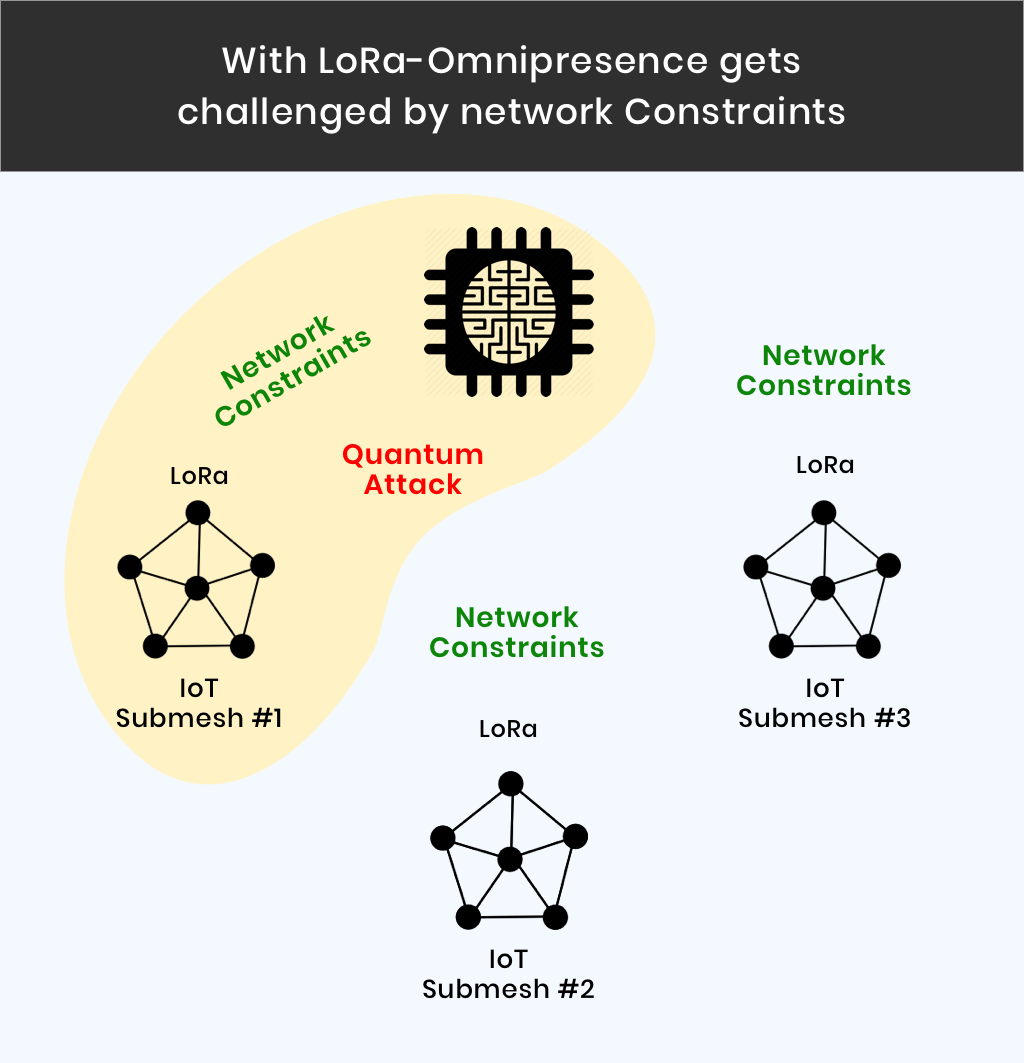
Under LoRa and similar massive IoT mesh networks, networks have very constrained transfer capacity. Here, even the most basic algorithms have to be further simplified, in order to make them effective.
So, building Omni presence is almost impossible as an IOTA network will most probably be made up a bunch of isolated mesh networks that are all connected through the internet.
In LoRa like networks that bandwidth is limited, not allowing any attacker or a super computer to connect with all nodes in a mesh network.
In part 2 of building Industrial IoT with IOTA, we will show you how to build a locker service that relies on IOTA’s token to allow accessing the content inside.