The year was 2019. Capital One looked at an ugly and possibly devastating data and security breach. The bank was using Amazon Web Services (AWS), and due to misconfiguration in its web application firewall, the attacker gained access to AWS storage and affected around 700 records. Because of this mishap, Captial One had to pay $190 million to 100 million people.
In a similar scenario, LinkedIn faced a humongous data breach in 2021. It affected over 700 million users. Here’s what happened – The attacker scraped the data by exploiting LinkedIn’s API and then posted it on the dark web, which impacted 92% of LinkedIn users. The data contained the users’ personal information and could have serious implications.
What’s astonishing is that Capital One and LinkedIn are two of the most successful SaaS applications and take the security of their SaaS products very seriously. Yet, they had to face cybersecurity breaches, which tells us that securing SaaS applications is essential. It’s easier said than done. More than 90% of public cloud security failures will happen by 2025.
With the advent of newer technologies, security for SaaS applications has become more complicated, with new threats or viruses. There are three reasons why cloud SaaS security is hard to achieve:
- Amount of users
- The lack of communication between business and security people
- Focusing more on features than SaaS security concerns
However, if you know the principles, challenges, and best practices associated with SaaS security, you can secure your SaaS product. This blog will cover all these aspects and minute details from a Chief Information Security Officer’s perspective.
What is SaaS security?
A set of best practices and policies implemented by SaaS providers to ensure the privacy and security of customers’ sensitive data privacy and security. SaaS applications have been on the radar of cybercriminals as they tend to provide plenty of sensitive data such as user’s name, DOB, credit card information, etc.
Therefore, organizations need to prioritize SaaS security initiatives. However, only 45% of companies have established a rapport between IT and security departments. To make matters worse, over 40% of SaaS data is unmanaged, increasing the chances for insider threats. The issue is complex, and the only way for SaaS security companies is to follow fundamental principles.
7 key principles of SaaS security
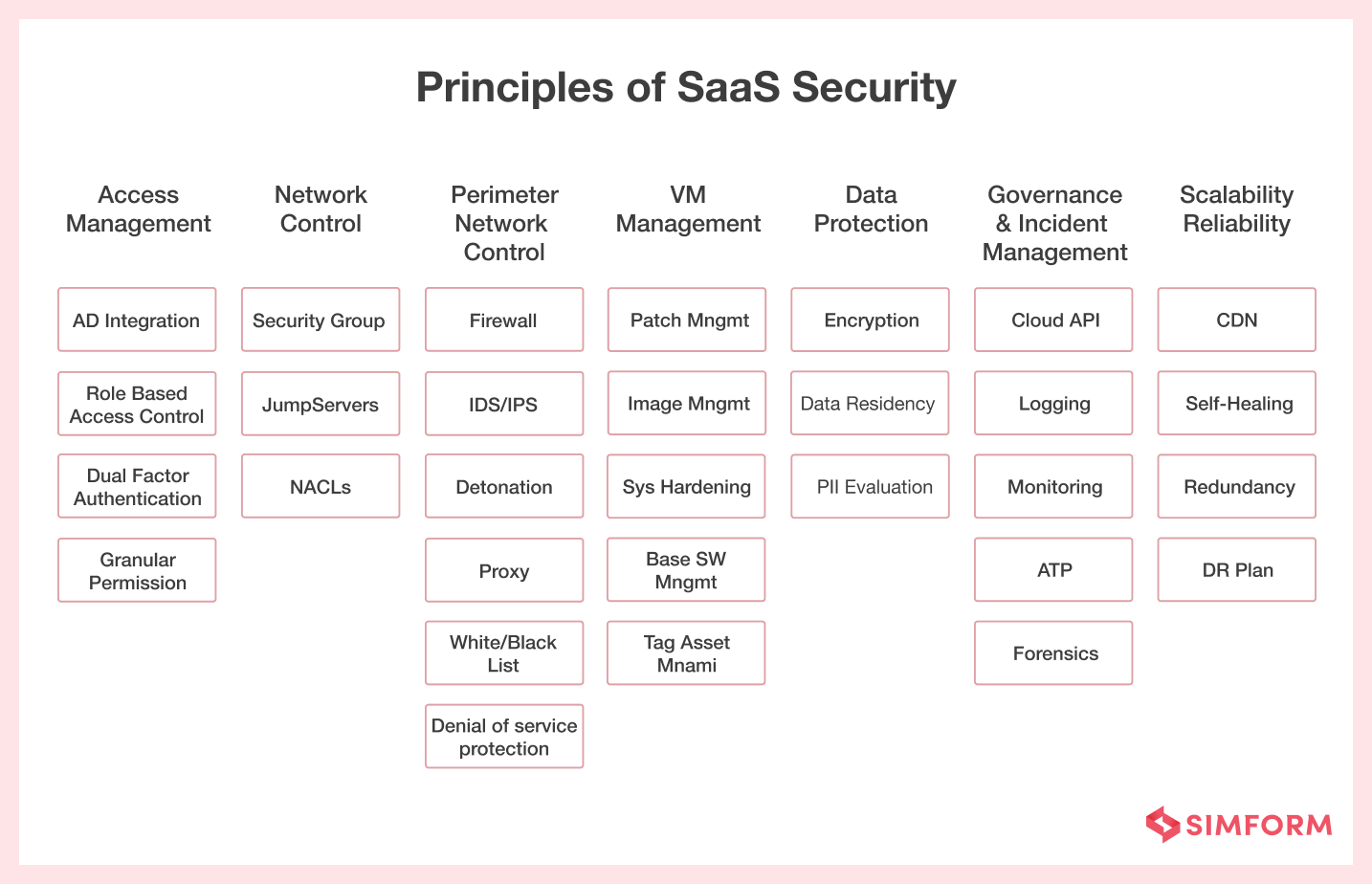
The Cloud Security Alliance recommends the following principles:-
1. Access management: The security personnel must understand access permissions. They should also work on role-based access control, system access control, and workflow management.
2. VM management: To secure your infrastructure, continuously update your VMs. CISOs should be aware of the security threats & patches and ask SaaS vendors to implement them.
3. Network control: CISOs should look at network access control lists (NACL) for granular network security details. They should create a Virtual Private Network (VPN) layer that acts as a firewall.
4. Perimeter network control: CISOs should prioritize firewall rules that filter out dangerous traffic from data centers. They should also use intrusion detection and prevention systems (IDS/IPS).
5. Data protection: CISOs should encrypt sensitive data for SaaS security. Moreover, they can separate duties at the client and server-side and conduct regular SaaS security audits.
6. Incident management: As a CISO, you should create an incident management system that captures, tracks, and monitors specific incidents. It will notify about security attacks in advance.
7. Reliability: SaaS apps should have high-level CDN, which minimizes downtime. Moreover, the system should have self-healing capabilities, and there should be a concrete disaster recovery plan so that Mean Time to Recovery (MTTR) is faster than ever.
SaaS security risks, issues, and challenges: A detailed overview
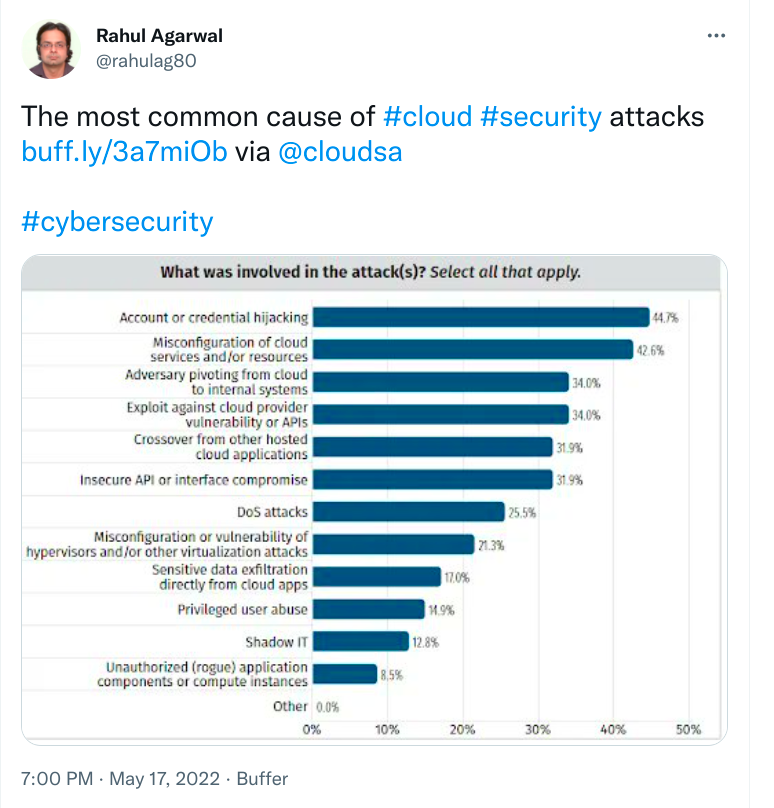
1. Identity and access management
Access management is one of the critical pillars that a CISO must include while developing a SaaS application security policy. However, it can also create a security gap that creates a backdoor for an attacker’s entry if not implemented properly.
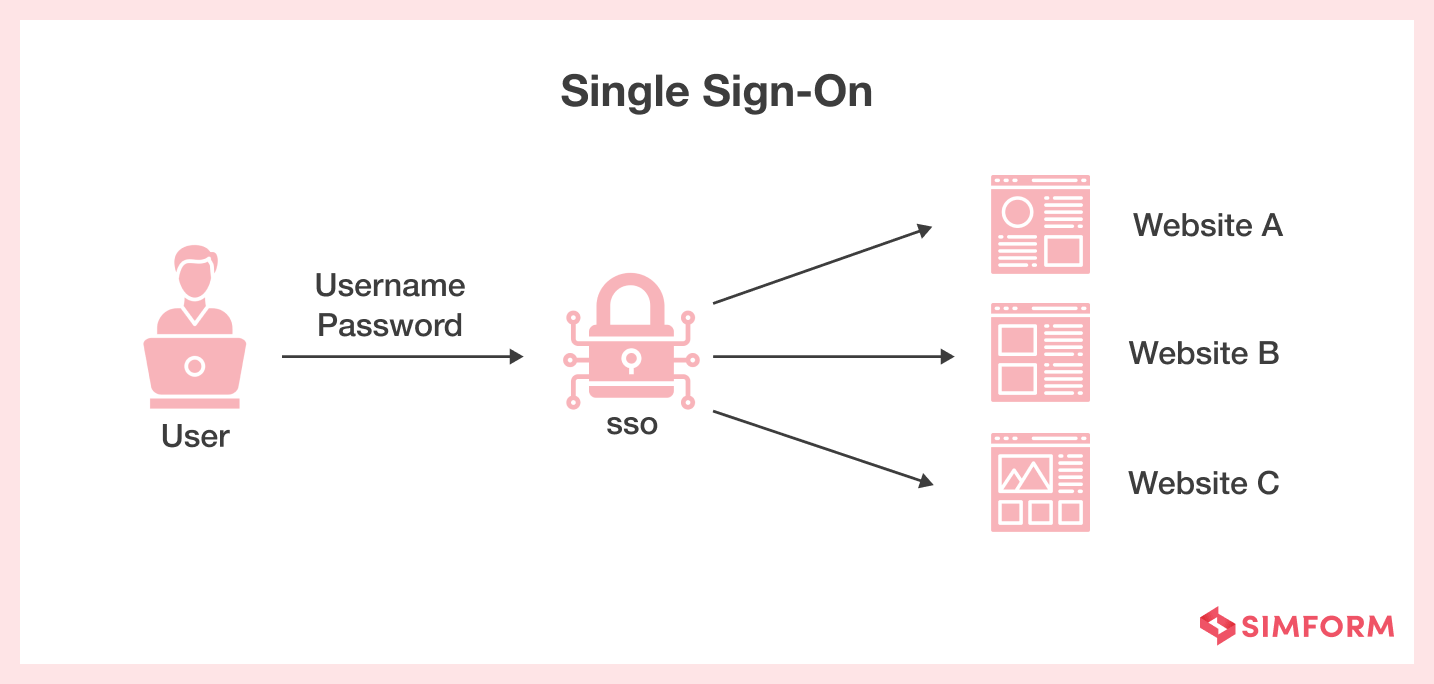
For example, Single Sign-On (SSO) and Secure Web Gateways (SWG) are effective ‘Identity and Access Management (IAM)’ techniques that SaaS providers implement. In SSO, the user has to log in only once, and they can gain access to all the related services under one ecosystem. However, SSO can bring along SaaS security risks if the provider doesn’t have a secure access system, as it allows easy tracking of ID and password and also accesses various services.
2. Virtualization
Most SaaS applications rely on virtualization as it has better uptime than traditional machines. However, if any virtual machine is compromised, multiple stakeholders could land in trouble as data gets replicated across servers. Over the years, virtualization has improved significantly in mobile app security, but there are still loopholes that hackers are bound to explore.
3. Obscurity
In the SaaS model, you focus on the application and business continuity, while physical infrastructure and architecture level decisions are left to providers. Sometimes, these providers don’t share any back-end details, which is a major red flag. CISOs should conduct one-to-one meetings with service providers and ask them about security considerations. Remember, a provider who can give satisfactory answers on data securities has to be your choice.
4. Accessibility
Any good SaaS app is accessible from anywhere. However, this advantage can quickly become a disadvantage if devices accessing the app are infected with viruses and malware. Also, if the user is accessing the app through public WiFi or VPN, it could invite security issues to your infrastructure. Therefore, CISOs should focus on securing all the endpoints to avoid such dangers.
NHS (National Health Service) is a UK-based publicly funded healthcare organization. The system comprises vast sensitive data, including patients’ healthcare information, doctors’ details, medicinal info, etc. Therefore, securing all the endpoints was critical. That’s when the institution collaborated with Cisco, which helped develop a unified security platform called SecureX. The NHS defends its highly targeted PII (Personally Identifiable Information) against online criminals through this solution. It also enables them to safeguard information from phishing attacks, ransomware, data exfiltration, etc.
5. Data Control
In SaaS, all the data gets hosted on the cloud, which means you don’t have much control over data storage and management. If something goes wrong, you are dependent on the providers. Therefore, whenever you enter a contract with the SaaS provider, ask about data storage patterns, security measures, and disaster recovery mechanisms. Once you get satisfactory answers, you can partner with the provider.
6. Misconfigurations
SaaS applications are known for providing many intricate functionalities into one product. However, they add layers of complexity to the code, which creates a chance for misconfigurations. Even a minor code mistake can affect your cloud services’ availability.
In one of the fatal misconfigurations in 2008, a Pakistani Telecom app tried to block YouTube due to some legal concerns. However, while blocking YouTube, they created a dummy route which caused misconfigurations, and YouTube remained unavailable globally for two hours.
7. Regulatory compliance
Regulatory compliance and governance policies are among the most critical aspects of managing the security of SaaS applications. As a CISO of a large enterprise, when conducting a SaaS security compliance check, ask your supplier this set of questions:
- Do your cloud services comply with regulatory, data, and privacy-related compliances such as GDPR, HIPPA, PCI DSS, SOX, etc.?
- Are you ready for a security assessment or audit of your cloud services?
- What are your governance policies, and how do you store the data of customers and third parties?
- Do you hold any security certifications such as ISO, ITL, etc.?
8. Disaster recovery
Whatever security measures you take to keep your application, server, infrastructure, and data safe, there is always a chance for disaster as it is unpredictable. CISOs should ask SaaS security solutions providers:
- What happens to all the data stored in the cloud in case of a disaster?
- Do you guarantee complete restoration of data?
- Is disaster recovery part of your service-level agreement?
- How long will it take to recover and get the data working?
SaaS security best practices
1. Vulnerability monitoring and testing
SaaS apps run on the cloud, and multiple users access them. Therefore, explicitly identifying malware and threats isn’t practical. Instead, a real-time SaaS application security testing system can detect vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Social Engineering, etc. It can also help you save a lot of precious time and cost. However, the question is, how to find a provider for SaaS security testing?
We got you covered! Simform helps you uncover hidden vulnerabilities and mitigate malicious threats with security testing services. We are a leading application development company that can be an extended tech partner. Over the years, our industry experts have collaborated with various SaaS firms and helped deliver robust and secure apps. So, get in touch with us.
In addition, many SaaS security tools are available in the market. You can use any of these automated tools to secure your application as it provides you with fixes and solutions to threats and vulnerabilities. A mix of manual and automated security testing for SaaS applications is a winning combination.
2. End-to-end encryption
Communication between server and user should happen over SSL (Secure Socket Layer), achieved through implementing the HTTPS protocol. Also, you should encrypt the data transferred as a query or reply. Moreover, multi-domain SSL certificates should also implement this approach. It helps you protect data and sensitive information such as personal details and financial information. Lastly, you could also take assistance from Active Directory (AD) with Security Assertion Markup Language, OpenID Connect, and Open Authorization.
3. Enforcing data security
CISOs should enforce multiple layers of SaaS data security standards to ensure that hackers can’t access sensitive information. You can’t eliminate the chances of cyber-attacks, but you can attempt to minimize them with high-tech security policies. Role-based access control, permissions, and task distribution can help you reduce data leaks to some extent.
Moreover, you should also have a clear policy about data deletion. There should be a data retention timeline in the service-level agreement, after which you should be able to wipe out the data and generate logs. This strict enforcement can help you in data loss prevention for SaaS apps.
CrayPay is a payment app that aims to ease the process of mobile payment in retail stores. With the payment gateway being an essential part, our team of certified professionals implemented point-to-point encryption, tokenization, and password protection. We also added multi-factor authentication, which helped CrayPay ensure reliability, and over 50,000 retailers use it.
4. Implementing VPN and TLS
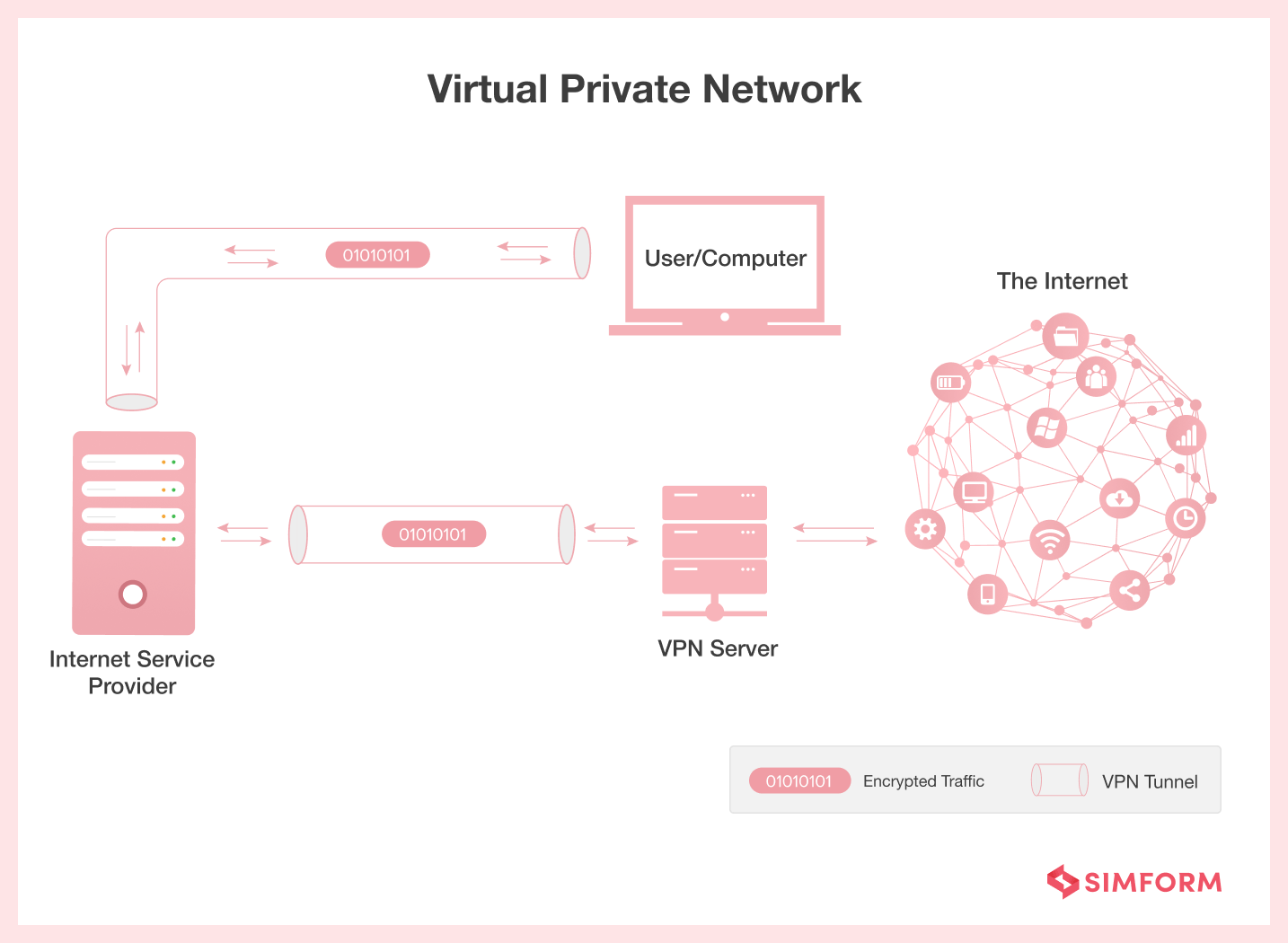
VPN (Virtual Private Network) ensures clients a safer working environment to store and manage their data. Instead of a simple multi-tenant system, it provides a better option as in VPN, you secure all endpoints of access, thereby protecting your infrastructure.
State Bank of India (SBI) is the largest nationalized bank in India, with an asset of $560 billion and over 27,000 branches. With such rapid growth, the financial institution must deal with security and regulatory challenges. As a result, the bank partnered with Trend Micro– a Japanese cybersecurity platform– which developed comprehensive security solutions for SBI. The solution delivers robust security capabilities for physical, virtual, and cloud servers. In addition, its single dashboard allows continuous monitoring of multiple controls across physical, virtual, and cloud environments. As a result, SBI has achieved optimal IT security across nearly 275,000 endpoints with a 99% update ratio and minimal process downtime.
Also, you should transfer SaaS through TLS (Transport Security Layer). It enhances the security of your data and improves the privacy aspect. It could be a default feature, or you could activate it through proper configuration and enforcement of security protocols. The same applies to the case of internal data and cookies, which you can secure by passing them through the TLS.
5. Managing user privilege and MFA
As a chief security officer of your SaaS company, you should implement the least privilege principle where users can access only certain application portions based on their role. If all users have the same access, cybercriminals can gain unauthorized access to your core system.
However, you can limit these situations with role-based access, as authentication is the most significant entry point. You can also take the assistance of MFA (Multi-Factor Authentication), where you must authenticate more than twice before accessing apps. Lastly, you can utilize the shared responsibility model that calls for accountability from each user.
6. Knowing OWASP updates
OWASP is an open-source web application security project that provides you with the latest updates related to security threats, vulnerabilities, malware, and attacks. It also enlists the best practices to overcome or prevent such situations. Knowing the newest OWASP updates should be a top priority for CISOs to overcome many security loopholes.
7. Conduct risk assessment
It is a core part of SaaS security monitoring initiatives that focuses on identifying technology assets with minimal risk, recognizing where data is stored and how it connects with business processes, evaluating the risk associated with data, etc. Regularly conducting SaaS security audits can help you mitigate the risk. A SaaS product is a mix of multiple applications, so conducting risk assessments is necessary. It will help you gain control over the crucial aspects.
Coca-Cola FEMSA is the largest franchise bottler of Coca-Cola trademark beverages globally. Jair García Osorio, CTO for Coca-Cola FEMSA, explains that when Coca-Cola decided to move to the cloud for efficient management, it felt the need for a comprehensive security assessment. The company then partnered with Micro Focus and adopted the Fortify on Demand solution. It helped Coca-Cola conduct risk assessments and identify/mitigate potential security risks before entering the environment. The solutions also helped Coca-Cola create a security framework that aligns with their business processes.
8. Use a CASB (Cloud Access Security Broker)
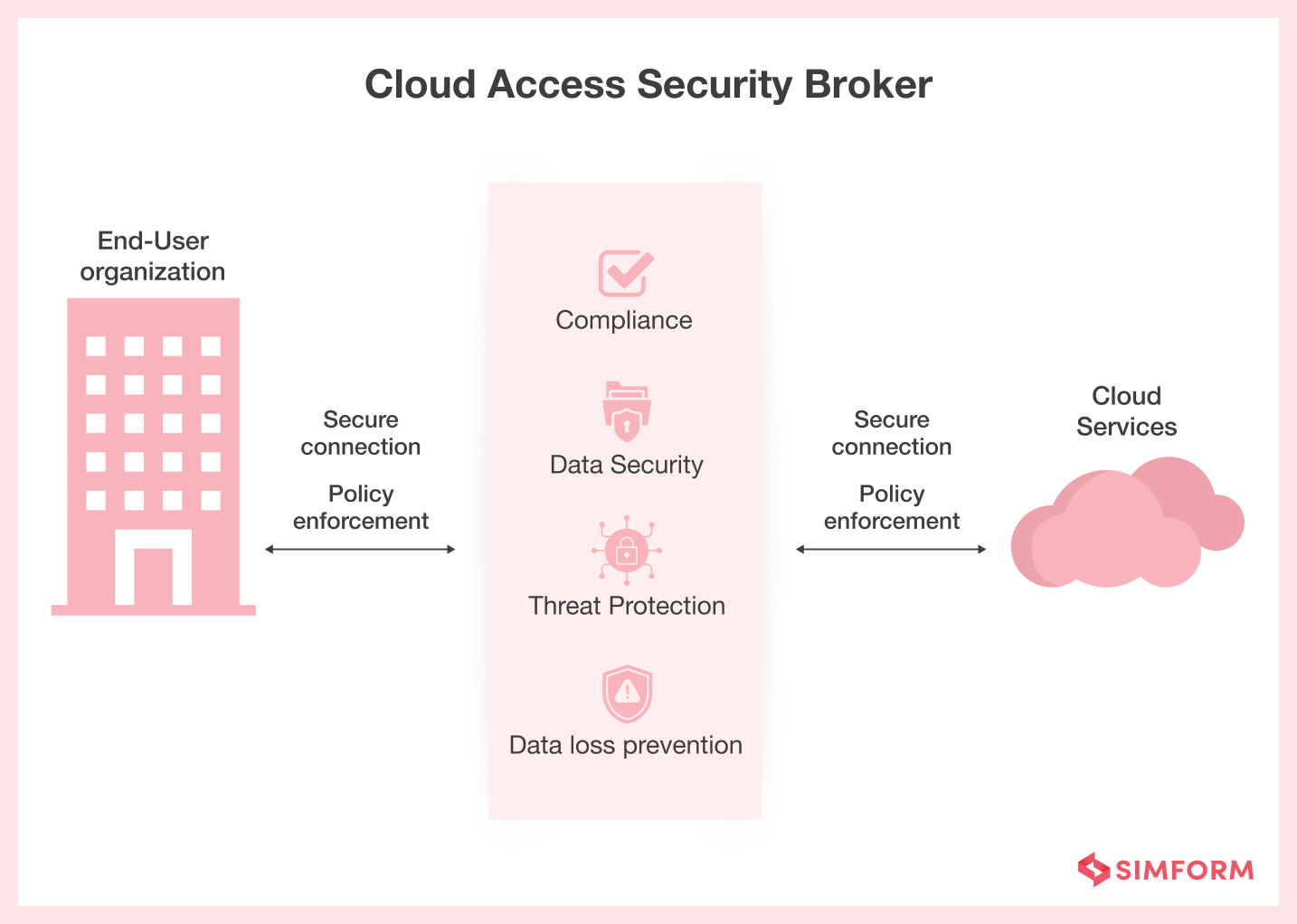
We have discussed some best practices that you should look for in your SaaS vendors. However, there will be instances where you wouldn’t be able to find the perfect match. In that case, the role of CASB (Cloud Access Security Broker) tools comes into the picture. CASB is an on-premise SaaS security software that enforces the security policies and places between end customers and SaaS service providers.
People use CASB tools to address cloud service risks, enforce security policies, and comply with regulations. There are four central pillars of CASB – (i) Visibility, (ii) Compliance, (iii) Data Security, and (iv) Threat Detection & Protection. Each of these components needs to play its role in creating the overall impact of CASB solutions. With CASB, you can simply add an extra layer of security.
9. Use an SSPM (SaaS Security Posture Management)
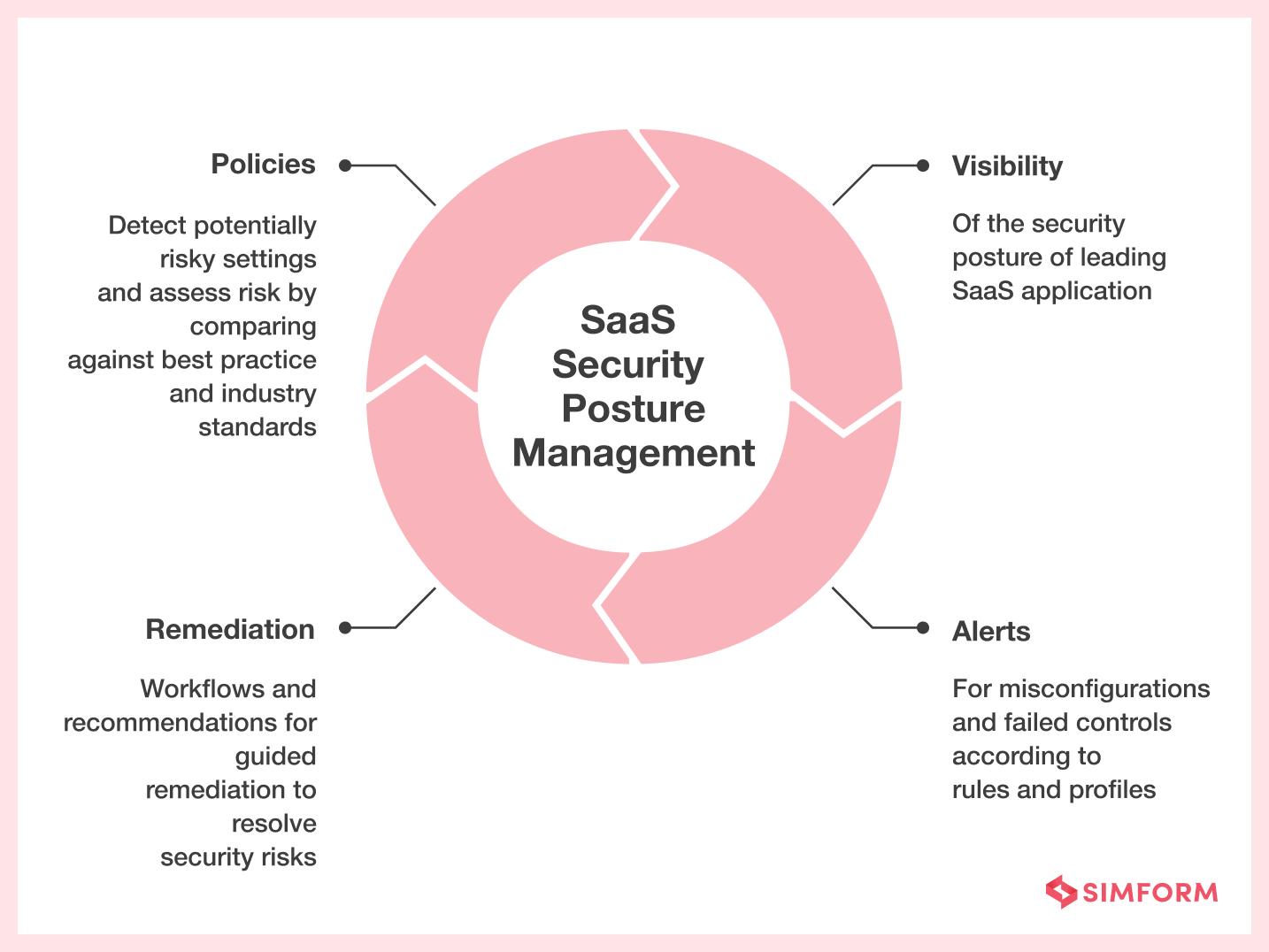
Security posture assesses the cybersecurity strength or security model. It includes various tools and techniques to safeguard users, devices, networks, and data. SSPM (SaaS Security Posture Management) refers to the ecosystem that enables you to automate continuous monitoring of SaaS applications to minimize risky configurations, prevent configuration drift, and support security and IT teams to ensure compliance.
It’s a subset of cloud security posture management that gives visibility, control, and compliance management capabilities to protect critical workloads and combat security challenges. Integrating SSPM into your ecosystem helps you rapidly detect misconfigurations, enforce compliance, and protect against insider threats and malware.
10. Discovery and inventory

In today’s day and age of high digital literacy, the software procurement process is not limited to IT departments but gets carried out by various employees. However, it can lead to security loopholes in the long term. SaaS security platform should maintain the inventory of all services.
Your information security teams should continuously track and monitor the usage of SaaS applications and identify unusual usage patterns. Many automated SaaS security monitoring tools can send alerts in case of security threats. Based on those inputs, CISOs can take appropriate action if required.
These are some SaaS security best practices that you should follow to safeguard SaaS apps. However, knowing the best methods is not enough for implementation purposes. You should also have a SaaS security checklist ready before enforcing security and governance policies, as it will help you know whether you’re on track.
A complete SaaS security checklist
Step 1: Developing a SaaS security guide
CISOs can meet with an internal security team, and experts can incorporate their suggestions regarding security vulnerabilities and risks. Finally, based on those inputs, you can create a guideline everyone should follow while evaluating any new SaaS tool for the organization.
Step 2: Employing a secure SDLC
SaaS security is an ongoing process. Therefore, you should establish security activities during the software development lifecycle. These activities comprise safe coding methodologies, vulnerability analysis, and penetration testing. It will also encourage the development team to conduct every phase from a security perspective instead of functionality.
Step 3: Ensuring secure deployment
You can perform secure deployment in two ways – (i) cloud deployment and (ii) self-hosted deployment. In the first scenario, the vendor takes care of the entire deployment process and ensures data security. In the second scenario, you’ve to ensure secure deployment without failures. As a best practice, try to automate the deployment as much as possible.
Step 4: Configuring automated backups
Not having data backups ready can be risky for SaaS solutions. So, focus on configuring automatic backups to assist you in disaster recovery or fatal failure. Recovering or retrieving data back is a far more manageable feat.
Step 5: Implementing security controls
SaaS security controls are specific measures to detect, mitigate, or reduce risks like data breaches or cyberattacks. Some essential security controls include:
- Malware detection
- Data encryption
- Identity management
- Access management
- Multi-factor authentication (MFA)
- Vulnerability monitoring and testing
Want to secure your SaaS app?
Accent Connect is an intelligent content management and distribution tool that aims to help organizations take their sales campaigns to the next level. The challenge was to secure the data as it’s a content-rich platform. We used AWS S3, where S3 does key management to encrypt files before saving them to disk and decrypt them when users request access to the file.
So, if you want to secure your SaaS app, you need a reliable partner who knows the nitty-gritty of SaaS and security policies. Well, look no further!. Simform is a leading SaaS application development company that can help you develop futuristic, reliable, and secure solutions. So, get in touch with our industry experts and avail a modernized, scalable, and robust SaaS product for your organization.

