What if, on a regular workday morning, your digital lifeline suddenly slips into the void! That’s what happened during an unexpected Slack outage. Users worldwide found themselves locked out when a routine configuration change spiraled into a full-blown system collapse. This incident, with over 11,000 reports logged at its peak, spotlights the undeniable importance of foolproof disaster recovery strategies.
The Slack outage underscores a harsh reality: no system is immune to failure, regardless of its size or scope. It highlights the need for robust disaster recovery plans, not just as an afterthought, but as a core aspect of IT strategy. This necessity is where AWS steps in, offering tools and services designed to build resilience into the very fabric of your digital infrastructure.
In this blog, we’ll dive into the heart of building system resilience with AWS. Discover the crucial elements of a disaster recovery plan and how AWS can protect your system from issues ranging from natural disasters to cyber threats.
Disaster Recovery Scenarios: AWS Services at Rescue
Disasters can strike unpredictably, affecting data and operations critically for organizations. To reduce such risks, AWS provides robust disaster recovery solutions. Here are the key AWS disaster recovery scenarios to consider for system administrators.
1. Natural Disasters
Natural disasters pose significant challenges to system administrators. Since 1980, the U.S. has faced 373 weather and climate disasters, totaling over $2.655 trillion in damages. This highlights the critical need for robust disaster recovery services which help in aiding system administrators in safeguarding their infrastructure against such natural catastrophes’ disruptive impacts.
Ensuring operational continuity and data safety in these unpredictable scenarios is crucial. AWS’s disaster recovery services provide a resilient solution, helping administrators protect their infrastructure against the disruptive impacts of natural disasters.
Amazon RDS and Amazon S3: These services are crucial for data backup and recovery, maintaining data integrity even during catastrophic events. They ensure that critical data is safely stored and can be quickly restored.
Amazon Location Service and AWS Ground Station: Used for mapping and damage assessment, these tools help organizations to understand the extent of the disaster and plan their response effectively.
Amazon VPC and AWS Direct Connect: They play a significant role in re-establishing critical internet connectivity in disaster-affected areas, enabling communication and coordination of relief efforts.
AWS Connect: This cloud-based contact center support service maintains essential communication lines during emergencies, ensuring that help can be coordinated and delivered where it is needed most.
AWS Lambda and Amazon EC2: These services allow for compute-intensive analysis in disconnected or remote environments, which is a key component in managing disaster scenarios effectively.
During Hurricane Ian in 2022, AWS’s role in disaster response was exemplified through its partnership with Help.NGO and the Information Technology Disaster Resource Center. They utilized various AWS services to create a common operating picture in the AWS Cloud, which was crucial for coordinating response efforts. This strategy included mapping, damage assessment, and establishing interim connectivity for community hubs like firehouses.
Such efforts provided significant support to first responders, relief organizations, and impacted individuals, showcasing the effectiveness of AWS in disaster management and recovery.
2. DDoS Attacks
DDoS, or Distributed Denial of Service attacks, are cyber assaults aimed at overwhelming network resources. They flood systems with traffic, obstructing regular operations and access. These attacks can severely disrupt an organization’s digital infrastructure, affecting both performance and stability. In the first half of 2023, the frequency of these attacks alarmingly rose by 31%, amounting to about 7.9 million incidents. AWS provides a robust defense against such threats with its suite of security tools.
AWS Shield Advanced: This service offers always-on detection and automatic inline mitigations that minimize application downtime and latency. It is specifically designed to protect against more significant and sophisticated DDoS attacks. AWS Shield Advanced is essential for businesses needing higher levels of protection.
AWS WAF (Web Application Firewall): This tool helps protect web applications and APIs from common web exploits that could affect application availability, compromise security, or consume excessive resources. By creating customizable web security rules, AWS WAF can block common attack patterns, such as SQL injection or cross-site scripting.
Amazon GuardDuty: This is a threat detection service that continuously monitors for malicious or unauthorized behavior. It helps identify potentially harmful activities within your AWS environment, including indications of DDoS attack attempts.
Amazon CloudFront: This content delivery network (CDN) is integrated with AWS Shield to provide an additional layer of defense against DDoS attacks. Its global network of edge locations can absorb large amounts of network traffic and distribute it, reducing the risk of any single point of failure.
Amazon Route 53: This scalable and highly available Domain Name System (DNS) web service is also effective in mitigating DDoS attacks. It routes end-user requests to infrastructure running in AWS, which can be scaled to absorb large DDoS attacks.
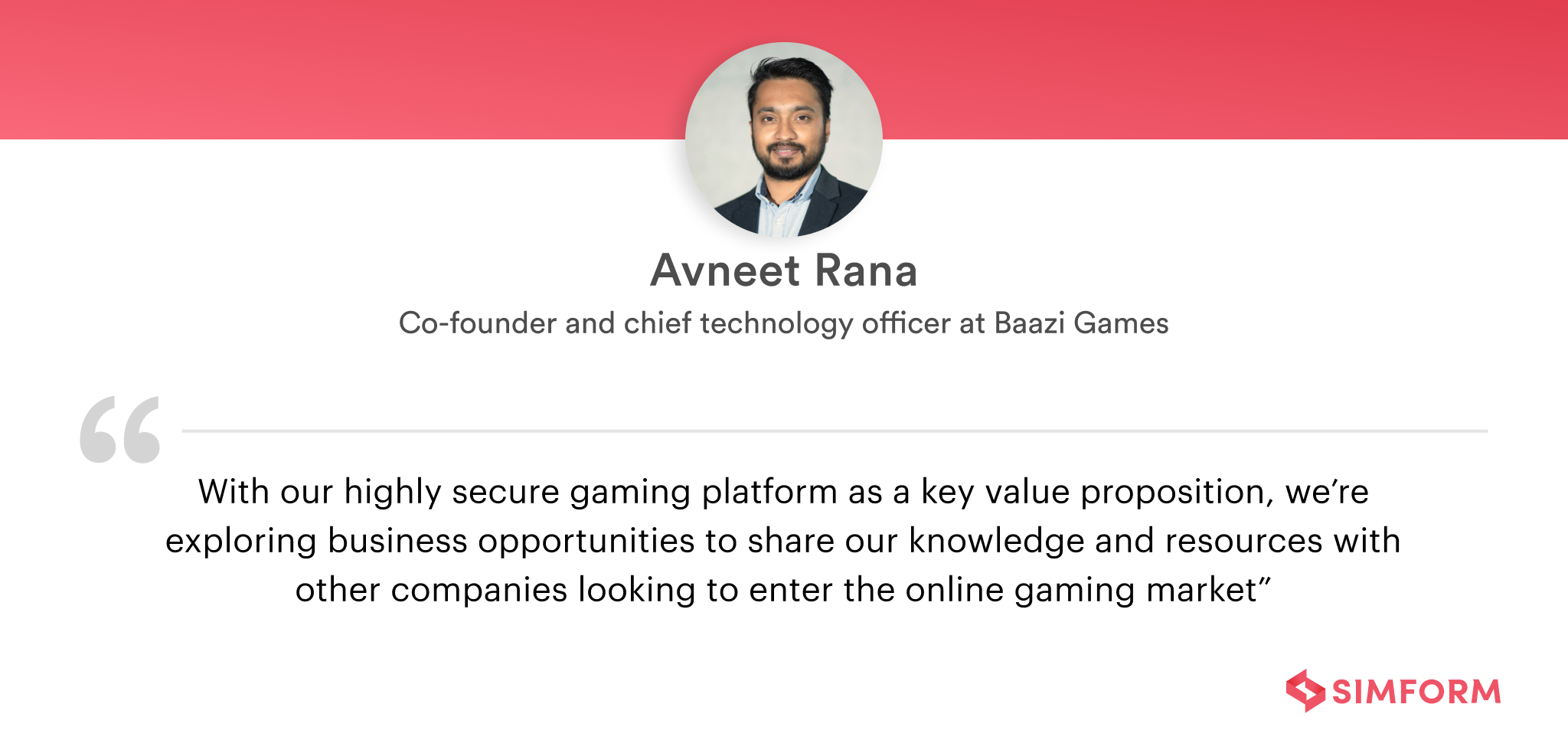
By strategically implementing these AWS services, organizations can significantly enhance their resilience against DDoS attacks. For instance, Baazi Games effectively used these AWS tools like AWS Shield advanced to counter over 50 DDoS incidents, ensuring continuous operation and business growth despite facing cyber threats. This approach underscores the importance of a comprehensive, cloud-based defense strategy in the current digital landscape.
3. Ransomware
Ransomware, a malicious software that encrypts data and demands payment for access, can devastate system architecture. It cripples critical operations by locking out essential data and systems. The impact on businesses is significant, as evidenced by the startling increase in attacks. In 2023, ransomware attacks rose by over 95% compared to the previous year, highlighting the urgency for robust defense and recovery strategies like those offered by AWS.
- Amazon Simple Storage Service (Amazon S3): Central in ransomware defense, Amazon S3 offers secure and scalable cloud storage, crucial for backing up critical data. Its reliability ensures data availability even under ransomware attack conditions.
- Amazon S3 Object Lock: This feature enhances data security by locking data versions during a specified retention period, preventing data manipulation and providing an additional security layer.
- Data Encryption: Prior to transferring to Amazon S3, encrypting data is a vital security measure. It plays a key role in protecting data against ransomware threats.
- Cloud-based Backup Integration: Integrating Amazon S3 with on-premises systems for data backup creates an effective defense mechanism. It ensures that production data is securely backed up and remains unaltered, safeguarding it from ransomware attacks.
Swiss public transport provider BERNMOBIL, aiming to enhance protection against ransomware, turned to AWS for secure, scalable cloud storage. Using Amazon S3 for backup, they achieved robust data protection against ransomware threats. The system stores 75 terabytes of data, with Object Lock ensuring data integrity.
The cloud-based solution complements BERNMOBIL’s on-premises system, offering an efficient, low-maintenance backup method, and plays a crucial role in their future IT strategy as they migrate more operations to the cloud.
4. Data Breaches
Data breaches, a serious concern in cybersecurity, involve unauthorized access to confidential data. Such incidents can lead to significant information loss and compromise system integrity. They not only affect data privacy but also disrupt operational continuity. The average cost of a data breach in 2023 is a staggering $4.45 million, highlighting the financial implications and the need for robust security measures. AWS offers tools and strategies to prevent and manage data breaches, ensuring system admins can maintain secure and resilient architectures.
AWS Backup: AWS Backup provides a centralized solution for backing up data across AWS services. By automating backup policies, it ensures data integrity and facilitates swift recovery after a breach. This service is essential for maintaining consistent data snapshots, enabling easier restoration.
Amazon GuardDuty: GuardDuty offers intelligent threat detection and continuous monitoring of AWS accounts and workloads. It identifies unusual activity patterns, potentially signaling a data breach, and provides actionable alerts, enabling quick response to threats.
AWS Shield: AWS Shield provides protection against DDoS attacks, a common cause of data breaches. It integrates with other AWS services to offer additional layers of security, ensuring that critical data remains inaccessible to unauthorized users.
AWS Key Management Service (KMS): KMS is vital for managing encryption keys used to secure data. In data breaches, protecting data at rest and in transit using encryption can prevent unauthorized access and data leakage.
DeepThink Health leveraged AWS to fortify its data security, reporting no data breaches and achieving over 99.9% uptime while complying with HIPAA and HITRUST standards. Using Amazon Redshift and AWS Security Hub, along with AWS WAF and Firewall Manager, they enhanced system, application, and data security, reducing data protection efforts by 30%. AWS’s scalable infrastructure, including Amazon EC2 and IAM, enabled rapid scaling and simplified data access for their distributed team.
5. Availability Zone Failure
An Availability Zone (AZ) failure refers to the breakdown of one or more data centers within a region. This can disrupt services and data accessibility, posing a significant challenge to system architecture. Such failures test the resilience of the cloud infrastructure, emphasizing the need for effective disaster recovery planning. AWS provides mechanisms to handle AZ failures, ensuring high availability and data protection.
Amazon Route 53: Amazon Route 53 plays a pivotal role in handling AZ failures. It intelligently routes user traffic to alternate locations, maintaining service accessibility and minimizing disruption. This DNS service is key for resilient responses to AZ disruptions.
Amazon Elastic Disaster Recovery (AWS DRS): AWS DRS is crucial for recovering from AZ failures. It minimizes downtime and data loss by quickly restoring cloud-based applications and data. AWS DRS is efficient for point-in-time recovery, ensuring business continuity.
Amazon RDS Multi-AZ Deployments: For maintaining database availability, Amazon RDS Multi-AZ deployments are indispensable. They offer high availability by replicating databases across different AZs, guaranteeing data access even during an AZ failure.
AWS Elastic Beanstalk: AWS Elastic Beanstalk facilitates the rapid deployment and management of applications. In the event of an AZ failure, it assists in swiftly transferring workloads to operational zones, ensuring consistent application performance and scalability.
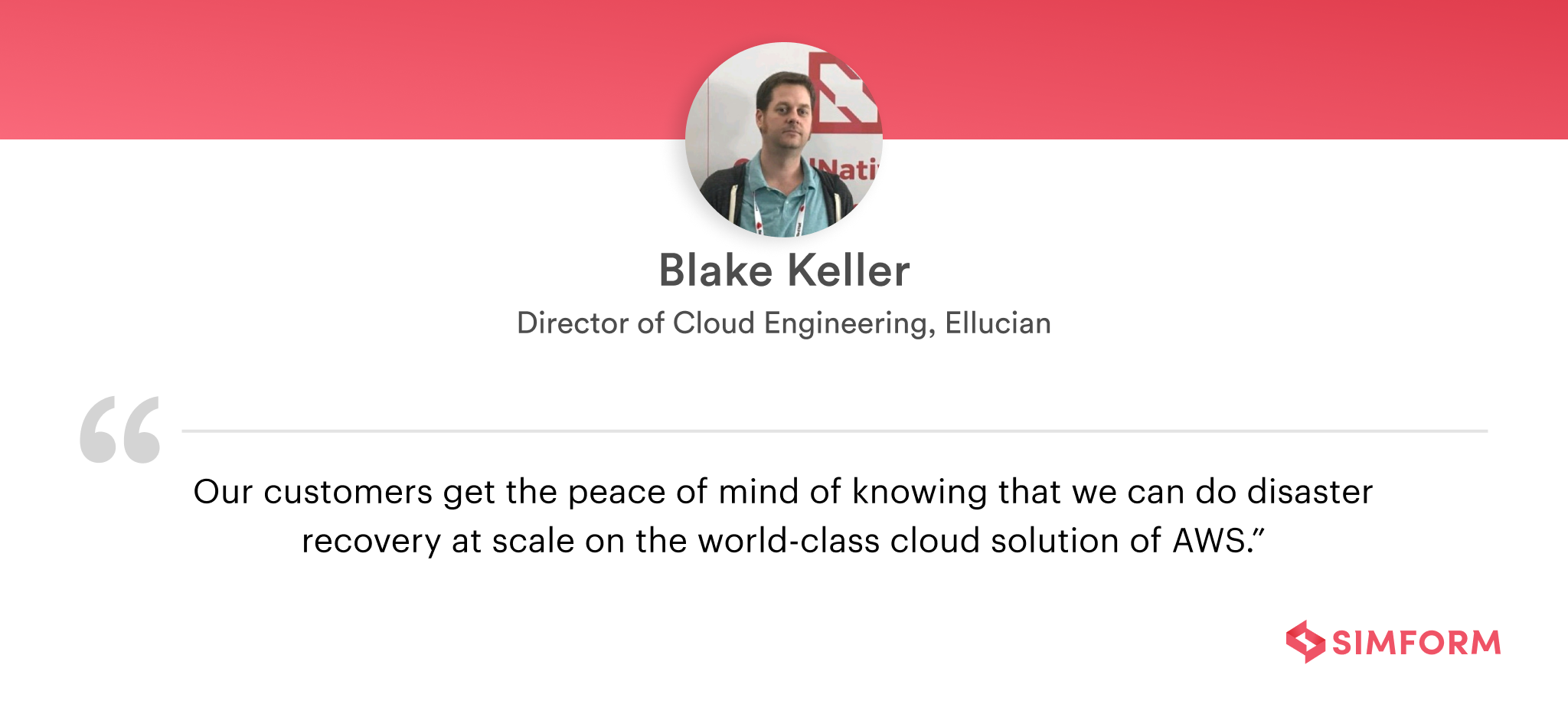
Ellucian, a leading provider of technology solutions for higher education, partnered with AWS to enhance its disaster recovery capabilities. By implementing AWS Elastic Disaster Recovery (AWS DRS), Ellucian significantly improved its recovery time and recovery point objectives by 15 times, while reducing maintenance costs by 21%. This innovative solution, integrating AWS DRS with serverless solutions and application-specific logic, ensures fast, reliable recovery of cloud-based applications.
Ellucian’s disaster recovery tests, using AWS DRS, are now 90% faster than before. This approach has not only optimized disaster recovery processes but also supports scalable infrastructure for future growth without increasing operational costs, ensuring robust, reliable disaster recovery for Ellucian and its customers.
6. Vandalism
Vandalism in the context of IT infrastructure refers to deliberate damage or disruption of physical or digital assets. It poses threats to system security and operational integrity. Such acts can directly impact the physical hardware or corrupt software systems, leading to data loss or service interruptions. It’s crucial for system administrators to consider vandalism in their disaster recovery planning. AWS provides robust tools to mitigate and recover from such incidents, ensuring data security and system integrity.
AWS Shield: AWS Shield offers protection against Distributed Denial of Service (DDoS) attacks, a common form of digital vandalism. It safeguards applications by blocking harmful traffic and ensuring operational continuity.
Amazon CloudWatch: Amazon CloudWatch enables real-time monitoring of AWS resources and applications. It detects unusual activities, alerting administrators to potential vandalism and allowing for quick response.
AWS WAF (Web Application Firewall): AWS WAF helps in safeguarding web applications from vulnerabilities that could be exploited for vandalism. It filters malicious web traffic, preventing unwanted access or data breaches.
AWS Backup: In the event of data vandalism, AWS Backup is essential for restoring data integrity. It provides reliable and secure backup across AWS services, enabling quick data recovery and minimal disruption.
In 2022, a severed fiber cable in Marseille, France, caused by vandalism, disrupted internet service across the U.S., Europe, and Asia for nearly a day. Zscaler CEO Jay Chaudhry confirmed the cause on LinkedIn, highlighting the incident’s resolution by the next afternoon. This event underscores the importance of resilience in cybersecurity and the role of system administrators in maintaining operational continuity.
Understanding these scenarios ensures a resilient approach to data safety and operational continuity. System admins can confidently manage unexpected challenges with these AWS solutions.
How to PrepareYour System for Disaster Recovery?
Preparing your system for disaster recovery is a crucial aspect of maintaining business continuity. A well-crafted disaster recovery plan ensures minimal disruption to operations during unforeseen events. Here are the key strategies to build resilience.
1. Assess System Vulnerabilities
Start by conducting a comprehensive system audit to identify potential risks. This process should include reviewing all hardware, software, and network configurations. Consider potential threats like cyber-attacks, hardware failures, and natural disasters. Evaluate the impact of these threats on business operations.
Prioritize vulnerabilities based on their potential impact and likelihood. Engage in regular vulnerability assessments to stay ahead of new threats. Use tools like AWS Inspector for automated security assessments. Document and track identified vulnerabilities for systematic resolution. Implementing a proactive approach is key to minimizing risks.
2. Calculate RPO and RTO
Recovery Point Objective (RPO) determines how much data you can afford to lose. It guides the frequency of your data backups. Recovery Time Objective (RTO) defines the acceptable downtime after a disaster. It helps plan for quick system recovery. Both RPO and RTO are crucial in shaping your disaster recovery strategy.
They should be realistically set based on your business operations. Regular assessment of these metrics ensures alignment with business growth. Accurately calculated RPO and RTO are essential for effective recovery planning. They influence the choice of technology and resource allocation for disaster recovery.
3. Use AWS Appropriate Services
AWS provides various services to support disaster recovery. Amazon S3 is essential for secure, scalable data storage and backups. AWS EC2 allows rapid provisioning of compute resources during recovery. Utilize Amazon RDS for database backup and recovery. AWS Elastic Block Store (EBS) offers persistent block storage for EC2 instances.
Amazon Glacier provides cost-effective archival storage options. Implement AWS CloudFormation for resource orchestration and management. Regularly explore new AWS features and services for enhanced disaster recovery capabilities. Selecting the right combination of these services is key to a resilient recovery solution.
4. Test Disaster Recovery Preparedness
Regular testing is essential to ensure your disaster recovery plan is effective. Simulate various disaster scenarios to evaluate your system’s responsiveness. This testing should encompass all critical components of your AWS infrastructure. Analyze recovery procedures for both data and applications. Check if RPO and RTO targets are being met during these tests. Involve different teams to understand the recovery process’s impact on various departments.
Document test results and use them to refine your recovery strategies. Frequent testing helps identify gaps and areas for improvement in your plan. A well-tested disaster recovery plan is crucial for business continuity.
Effectively preparing your system for disaster recovery on AWS mitigates risks and enhances business resilience. Implementing these strategies ensures that your organization can withstand and quickly recover from disruptive incidents.
What are the Key Elements of a Disaster Recovery Plan?
Apart from knowing the common disaster recovery scenarios and their solutions, one must also know a few key elements of a robust disaster recovery plan. Understanding these elements helps system administrators create a comprehensive approach to disaster preparedness.
1. Budget
Allocating a sufficient budget is key for disaster recovery, balancing the cost of resources and technologies. This includes initial setup and ongoing maintenance, emphasizing critical areas and overall plan feasibility. Adjust the budget regularly to meet changing needs and technologies.
2. Resources
Essential to disaster recovery are personnel and infrastructure. Skilled staff handle plan execution and maintenance, while physical facilities like data centers must be secure and redundant. Continual training ensures resource readiness.
3. Internal and External Communication
Effective internal and external communication is crucial during disasters. Establish clear protocols and equip teams with reliable tools. Regular drills refine these processes, ensuring everyone knows their roles in emergencies.
4. Recovery Timeline
A defined recovery timeline minimizes downtime. Set realistic goals for system restoration and prioritize essential operations. Continuously monitor and update this timeline to align with business objectives.
5. Management’s Position on Risks
Management’s risk perspective shapes the disaster recovery plan, balancing preventative measures and recovery capabilities. It determines acceptable downtime and data loss levels, guiding investment decisions.
6. Technology
Select technologies for data integrity and rapid recovery. Regular assessments and investments in scalable, reliable solutions like cloud-based options are vital.
7. Data
Protect critical data with continuous backups and secure storage. Regularly test data recovery processes for integrity and availability.
8. Suppliers
Choose reliable suppliers and maintain strong relationships. Their understanding of your recovery objectives is crucial for effective support.
9. Compliance Requirements
Adhere to industry regulations and standards. Regular audits ensure compliance, with documentation maintained for verification. Stay informed about legal changes to adjust your plan accordingly.
Incorporating these elements into your plan fortifies your organization against potential disasters. It’s a strategic step towards maintaining operational resilience and data integrity.
How Simform has Helped Businesses Build Disaster Resilient Systems with AWS?
Building disaster-resilient systems is crucial for business continuity. Simform has been at the forefront of using AWS to enhance system resilience. Here are the ways we have empowered businesses to overcome disaster recovery challenges.
The FIH portal
For the Hockey World Cup’s web presence, Simform developed a resilient and scalable website to handle over 3 million viewers in Asia, using AWS S3 and CloudFront. A headless CMS and React.js enabled adaptable content delivery under high traffic. Automated testing tools and AWS CloudFormation streamlined deployment, showcasing our digital product engineering expertise.
A Marketing Analytics Platform
Faced with scalability and security challenges, a marketing analytics platform benefited from Simform’s migration to AWS EKS. This move reduced latency by 30% and infrastructure costs by 30%, while significantly improving resilience. Features like Karpenter for auto-scaling, Nginx for load balancing, AWS KMS for encryption, and AWS IAM for access control enhanced performance and security. Monitoring tools like Grafana and Prometheus ensured proactive issue management, demonstrating Simform’s commitment to efficient, secure solutions.
Our expertise in AWS technologies solidifies client disaster recovery strategies, ensuring robust, agile systems.
Choose Simform and Ace Disaster Recovery
Choose Simform and excel in disaster recovery strategies on AWS. Our team comprises over 200 AWS‑certified experts who specialize in comprehensive disaster recovery solutions. We have a wide range of AWS Service Validations, including AWS Lambda, Amazon CloudFront, and Amazon EKS.
Our AWS expertise helps us architect robust systems that withstand disruptions. Backed by competencies in SaaS, DevOps, and Migration Services, we ensure your infrastructure is not just resilient but also optimized and future-proof. Partner with Simform to leverage our advanced AWS capabilities and safeguard your business against the unexpected challenges with confidence.