API brings many benefits and plays a significant role in software and application development. According to Salt Security, 95% of enterprises had API security breaches as of Q1 2022. According to an estimate, USD 12-23 billion is the average annual API-related cyber loss in the US alone. No wonder several IT decision-makers today are scratching their heads about API security with more and more data-centric projects. The security enigma around APIs is why most experts recommend following industry best practices.
It might look like simple maintenance with a basic understanding of the APIs, a well-organized inventory, and documentation, but API security is more complex. This article helps you understand the top 20 API security best practices to know how you can safeguard web app APIs effectively.
What is API security, and what are its primary aims?
API security is the procedure of preserving cybersecurity threats and attacks from APIs. Having proper API security measures ensures all requests coming to APIs are from legitimate sources and are valid. Moreover, all the responses sent to the client side should get encrypted, not allowing attackers to take advantage of data exposures.
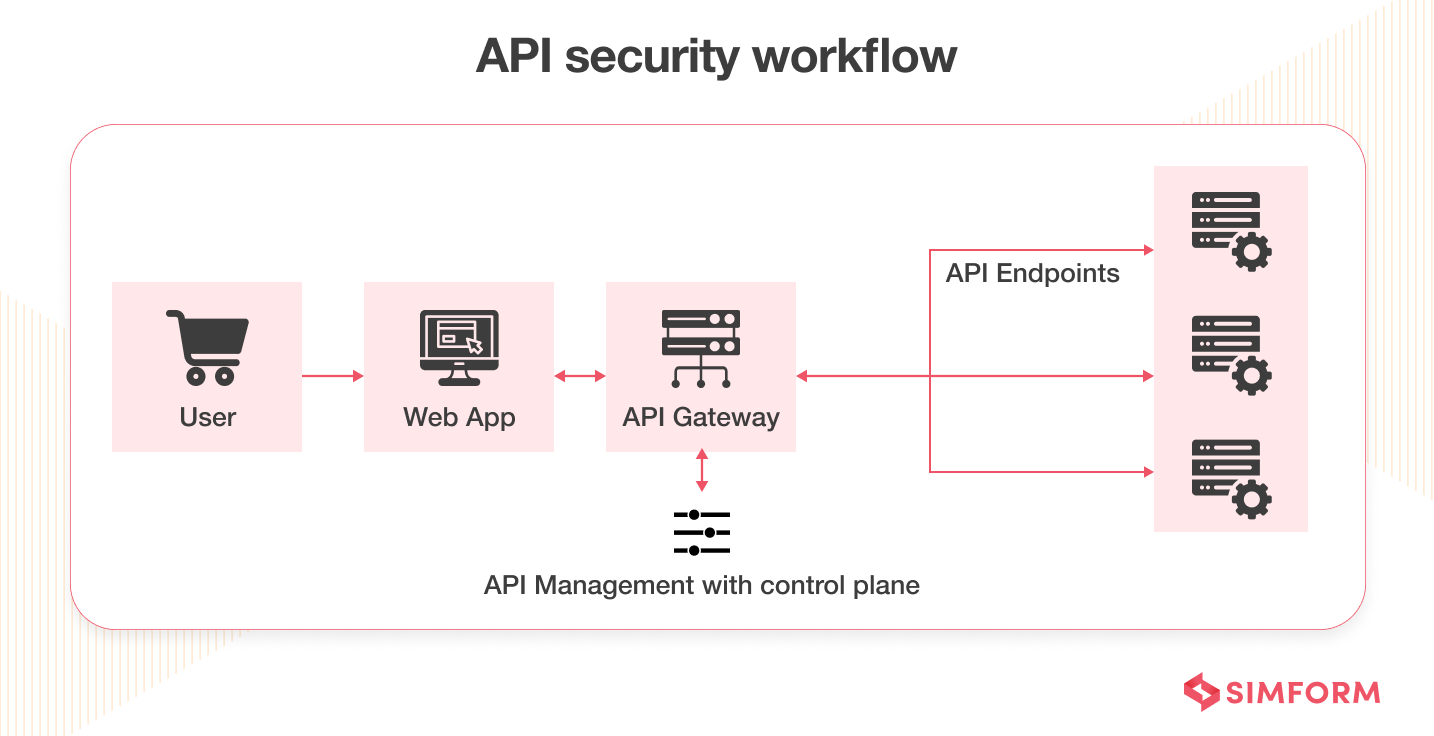
The primary aim of REST API security is to ensure API requests are
- Authenticated
- Authorized
- Validated
- Cleansed
Also, API security should allow you to process APIs even under a tremendous load. A modern application comprises several API endpoints that use different protocols and request formats. Thus, protecting them with standardized practices is vital.
With the basics of API security known, let us dive into more details and analyze why API security matters the most today.
Why is API security important?
A modern application comprises several API endpoints that use different protocols and request formats. Thus, protecting them with standardized practices is vital. Various APIs present a larger attacking surface for intruders to steal sensitive data. Insecure APIs are severe threats as they’re the most exposed component of network resources.
For example, API vulnerabilities in online services from Coinbase exposed users’ personal information and facilitated faulty transactions. The detailed analysis found that this mishap was due to broken-object level API authorization, one of the most common attacks and OWASP top API security vulnerabilities.
83% of all web traffic comes from APIs. 98% of enterprise leaders agree that APIs are critical to digital transformation. However, surveys have shown that 95% of companies have faced API security attacks during 2022, which have increased by 681% between 2021 and 2022. That is why API security has become a crucial aspect of modern-day web applications.
Before securing an API, let us understand the most common API security vulnerabilities you need to overcome in the upcoming section.
Most common API security vulnerabilities
The following are the most common API security vulnerabilities you need to address while developing your web application:
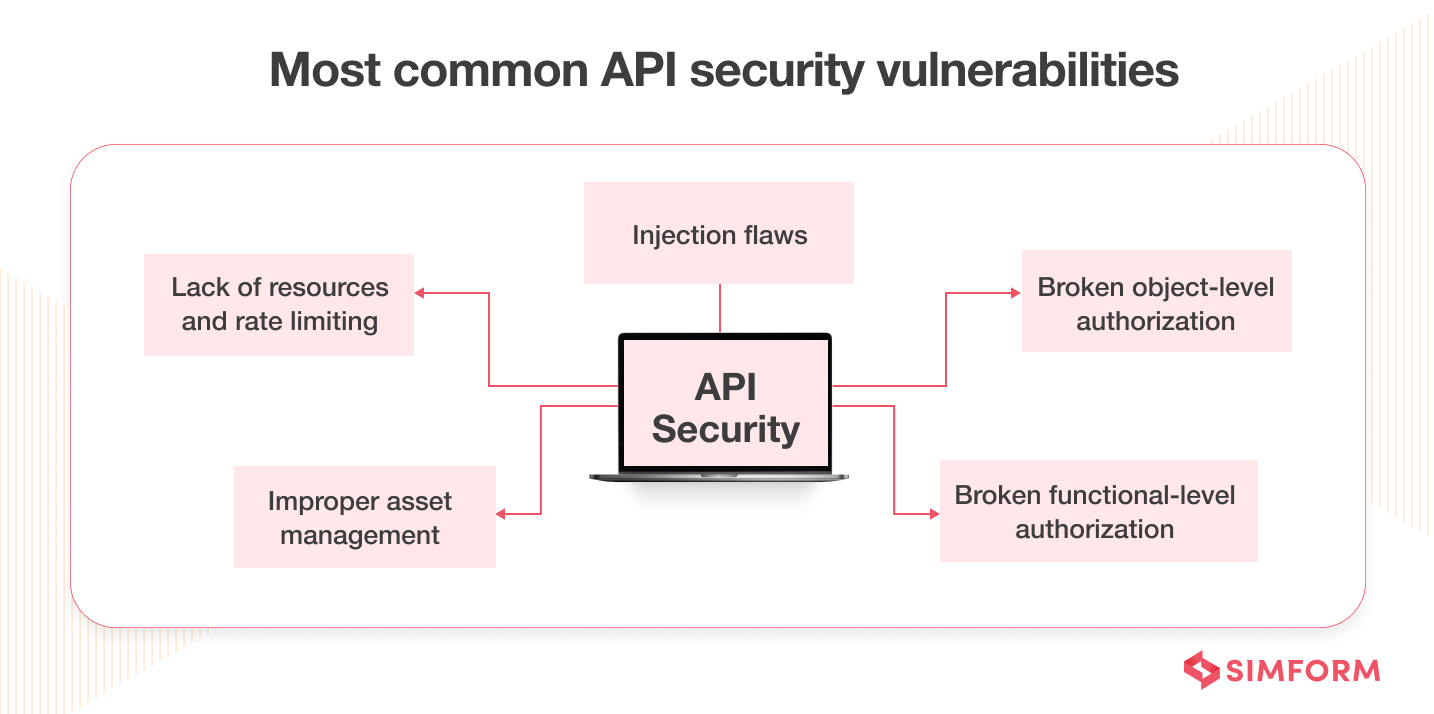
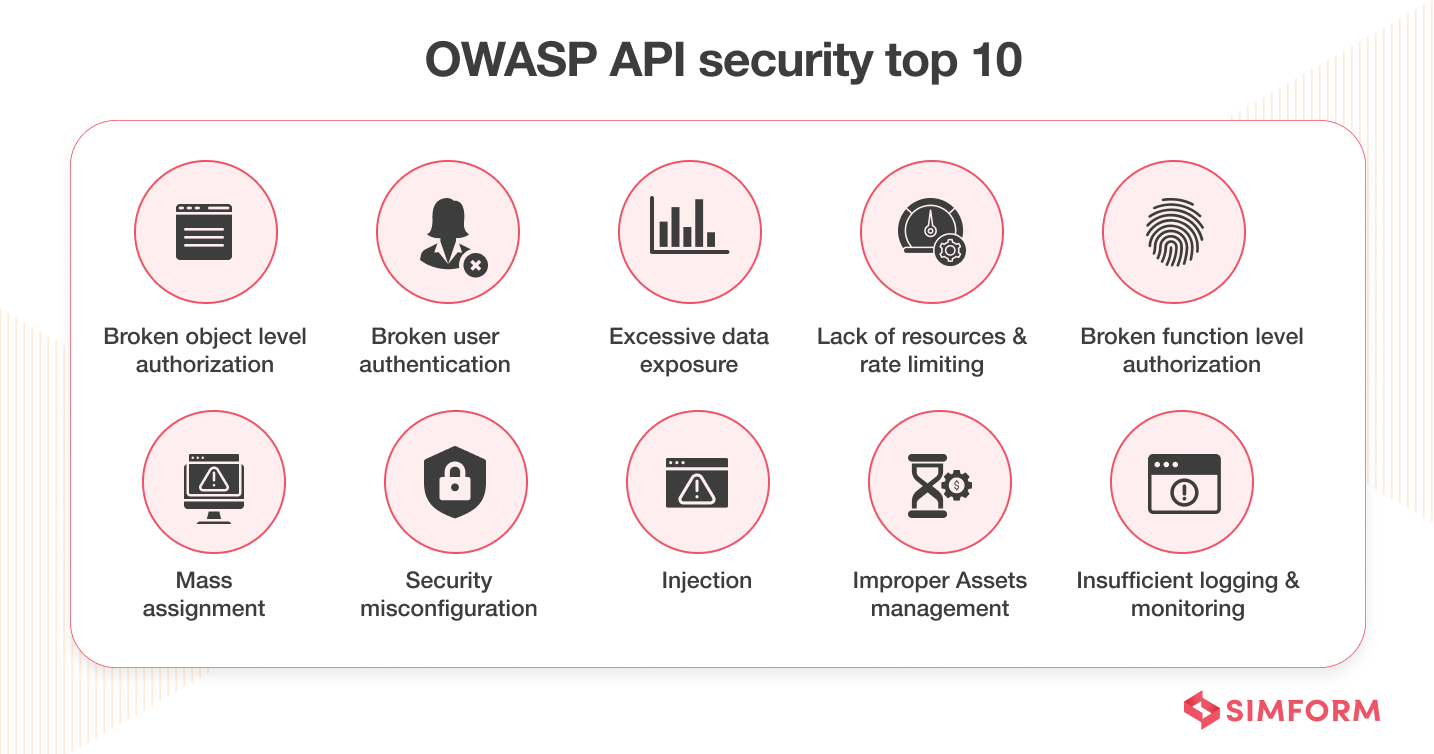
- Broken object-level authorization: It occurs when a request can access or modify data the requestor hasn’t had access to.
- Broken functional-level authorization: It arises when the principle of least privilege hasn’t been implemented due to complex access policies.
- Excessive data exposure: It occurs when API responses to a request return more data than necessary.
- Improper asset management: It occurs when you don’t have thorough documentation and a repository of APIs.
- Lack of resources and rate limiting: It happens when there is no limit on the number and size of requests.
- Injection flaws: It occurs when data is not parsed and validated correctly.
These were some of the most common or known vulnerabilities related to API security. With problems known to us, let us focus on the possible solution by discovering API security best practices in the next section.
API security best practices
1. Authenticate and authorize
You must control their access to secure APIs used for traditional web applications. For that purpose, comprehensively identifying authentication flaws and authorization flaws related to users and devices becomes paramount. You can achieve all of these with stringent authentication methods and authorization policies. All the client-side applications must include a token in the API call for authenticating the user’s identity.
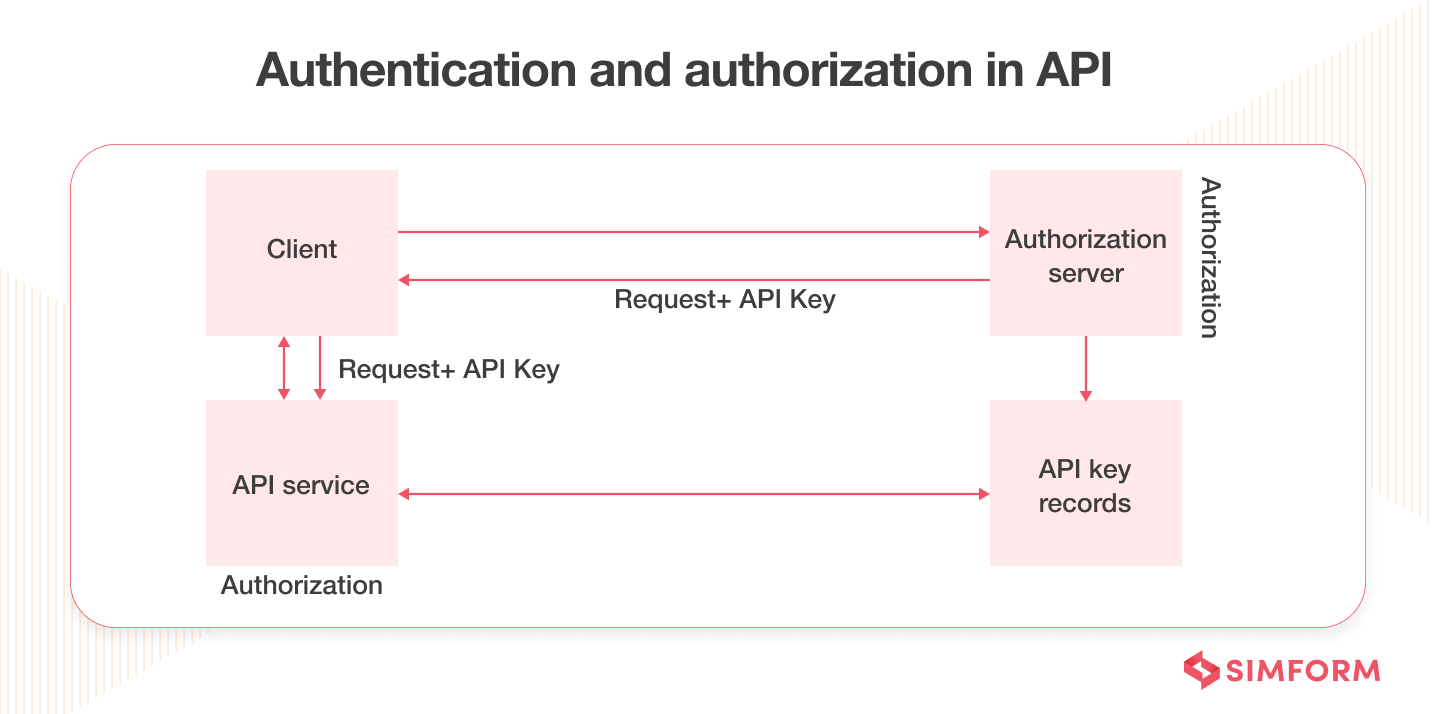
- You can use standards like OAuth 2.0, OpenID Connect, and JSON web tokens for basic authentication of API traffic.
- You can also define access control rules or grant types for particular user groups and assign role-based access.
- Lastly, you can enforce POLP (Principle of Least Privilege) access where you minimize permission to ensure web application security.
For example, if a user just needs to read a blog or post a comment on it, only that much permission should get granted. You should not give editing privileges or any different permissions to such user bases. It helps you to minimize the critical security risks involved in API calls.
2. Encrypt request and response
In a web application that involves a lot of user interaction, there is bound to be a lot of network traffic. As someone dealing with security concerns, you should emphasize encrypting that network, specifically the API requests and responses. It is because those APIs comprise sensitive data or authentication credentials that hackers can access easily.
Moreover, you can also have policies that force the developers to use HTTPS standards for all APIs. Enabling HTTPS, where possible, is a better solution than directing the traffic to HTTP, as most APIs contain sensitive user credentials and data.
3. Validate the data
Never assume that there is a proper data validation mechanism for APIs. Consistently implement your cleaning and validation server routines on the server side. It will help you to prevent risks like Code Injections or SQL Injection attacks, CSRF (Cross-Site Request Forgery) attacks, and CSS (Cross-Site Scripting) attacks. In any successful attack, the attacker tries to insert a malicious script into the source code. Use JSON or XML Schema Validation to counter such security threats.
Tools such as Postman and Chrome DevTools can help as they can examine the data flow for all of your APIs and discover errors or anomalies involved.
For example, in 2020, Axis Bank’s newly formed Digital Business and Transformation (DBAT) team implemented considerable change, especially in microservices for various utilities. In this scenario, communication was a real challenge with different microservices spread over the distributed architecture. That’s where Axis Bank opted for Postman. It helped them have better collaboration among various utility services. Also, it reduced development pipelines from 6 months to 1 month.
4. Implement access control
Organizations nowadays prefer using third-party APIs to facilitate rapid development. Also, there is an issue of API Sprawl; a drastic increase in the number of APIs has resulted in less visibility of the APIs in your digital estate.
However, developers are unaware of third-party APIs’ security practices. In this scenario, it’s best to have access control that manages who, what, and when there’s an API (Application Programming Interface) call from third-party vendors. It also checks data access, creation, update, and deletion.
Another thing you can implement for access control is keeping your APIs behind the web application firewall, which gets access through a secure protocol such as HTTPS. API firewall can query given resources and helps you to prevent signature-based and injection-based threats. Lastly, you can also enforce geo-velocity checks to protect against unauthorized access from an unknown location.
Some of the most common examples of access control are having access cards for office check-in or check-out, biometric access to the server room that contains sensitive data, PIN identification at the ATM for withdrawing money, etc.
5. Share necessary information
API responses comprise many data records rather than relevant information. It’s on the client application what they want to show to a valid user. You can call it lazy programming, where developers haven’t been responsible for protecting sensitive data.
In this scenario, the malicious actors will have a vast playground, thereby increasing the chances of data leakage. They can use techniques like credential stuffing to gain a foothold on an endpoint device. So, developers should ensure that the response should comprise the minimum information required to fulfill a specific request.
For example, if there is a request for an employee’s age, only that number should be the ideal response. You shouldn’t include data of birth as additional information.
6. Assess API risks
Conducting risk assessments of your APIs is one of the most important steps you can take to safeguard your data. Craft security policies that helps you measure whether the web application’s API meets security standards and is not vulnerable to risks.
The OWASP API Security list that comprises the top 10 OWASP vulnerabilities is a good list to keep yourself updated about the latest security risks.
- A thorough risk assessment should identify all systems and data affected. You can then devise a concrete plan of the steps you need to take to reduce the risk to an acceptable level.
- Also, whenever there’s any modification in the API or new threats are on the rise, you should review the documentation made for risk assessment and repeat the procedure.
- Lastly, use this documentation before making any changes to the source code to check mobile app security.
7. Record APIs in a registry
Anyone who doesn’t have any idea about the number of APIs involved in the web application won’t be able to secure it. The reason is the drastic increase in API consumption in modernized web applications. Therefore, it becomes paramount to record all the APIs in a registry. You should have parameters such as
- Name
- Purpose
- Payload
- Usage
- Access
- Live date
- Retired date
- Owner against every API record
It will help you keep track of API payloads used in web applications and save time you sometimes waste while revisiting the same API twice.
The record of information should also include logging, which helps you know what, when, and who utilized the API. It also enables you to meet compliance and audit requirements. Rich documentation during the course of API lifecycle will also help third-party developers use the APIs developed by you. API registry should also include technical requirements like functions, classes, return types, arguments, etc.
8. Stash your API keys
API keys identify and verify access to the application. They can also block or throttle calls made to APIs and discover usage patterns. API keys are less secure compared to authentication tokens and require careful management.
You should avoid embedding API keys directly in the source code. Instead, store them in environment variables or files outside the app’s source tree.
You can use a secret management service to protect API keys.
You should keep deleting unwanted API keys and re-generate keys periodically.
9. Carefully choose web service APIs
There are two options to access web services via APIs –
- Simple Object Access Protocol (SOAP), a communications protocol
- Representational State Transfer API (REST API or RESTful API)
Both of these formats require different strategies to ensure robust security.
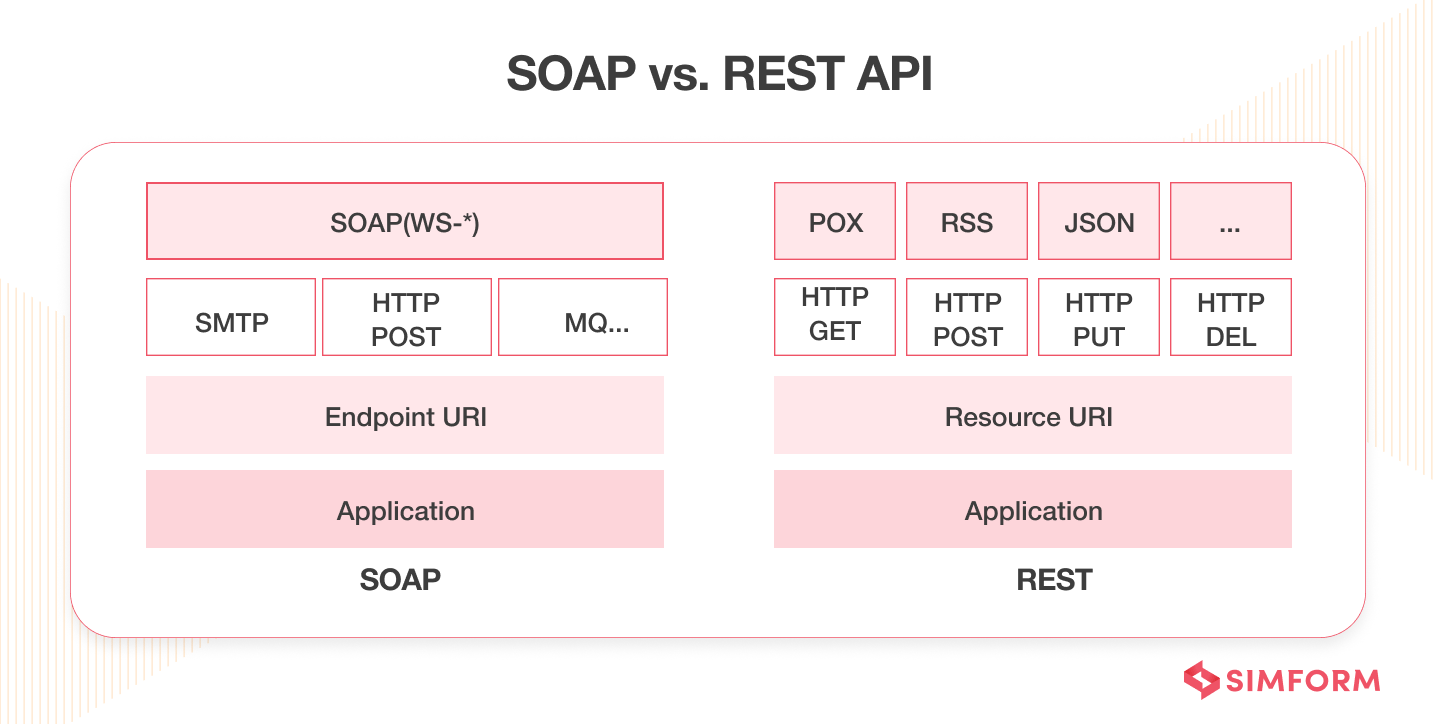
SOAP security gets applied at the message level using digital signatures, while REST heavily relies on access control rules associated with HTTP tags and URL paths. So, carefully choosing the web service APIs is paramount in achieving business goals. While SOAP helps you with standardization and security, REST provides easier access to web services.
SOAP can only handle XML and HTTP formats, while REST can conduct identity verification for multiple data formats such as JSON, comma-separated values, and HTTP. So, both web services have their distinct pros and cons. It all boils down to the individual needs of the businesses then.
Generally, for stateful operations, one should opt for SOAP APIs. For example, performing repetitive, chained tasks for banking application that requires you to retain specific client data within the server. That’s where SOAP APIs can be helpful. On the other hand, REST APIs are valid primarily for stateless operations. It helps develop public APIs. Some famous examples of REST APIs are Gmail and public APIs related to health, jobs, cryptocurrency, and machine learning residing on GitHub.
10. Enforce AI-based API monitoring and threat detection
AI-enabled behavior analysis can improve API security. It helps you to set the benchmark for regular API traffic, reduce API abuses, and provide visibility into consumption patterns. Developers can fine-tune the threshold settings for context-based security control checks. Any threat detection tool can use this information to discover abnormal behavior to flag or stop a potential security incident.
Attackers repeatedly check APIs to find granular details about them. They have malicious purposes of finding something in your source code that they can exploit. Therefore, AI-based monitoring can help as it provides you with a list of grey areas in applications that attackers can exploit. Overall, it will help reduce the chances of any severe threats in the application. Also, the approach doesn’t requires predefined policies, rules or attack signatures.
Tools like Sematext Sythetics, Site24x7 Website Monitoring, AppDynamics, Graphite, Prometheus, etc., can help you in API monitoring and threat detection.
11. Conduct security tests
To secure your APIs, you must be proactive rather than reactive. Don’t wait for any security attacks to conduct a root cause analysis of the threats. Instead, conduct rigorous security tests from the beginning of the web application development process.
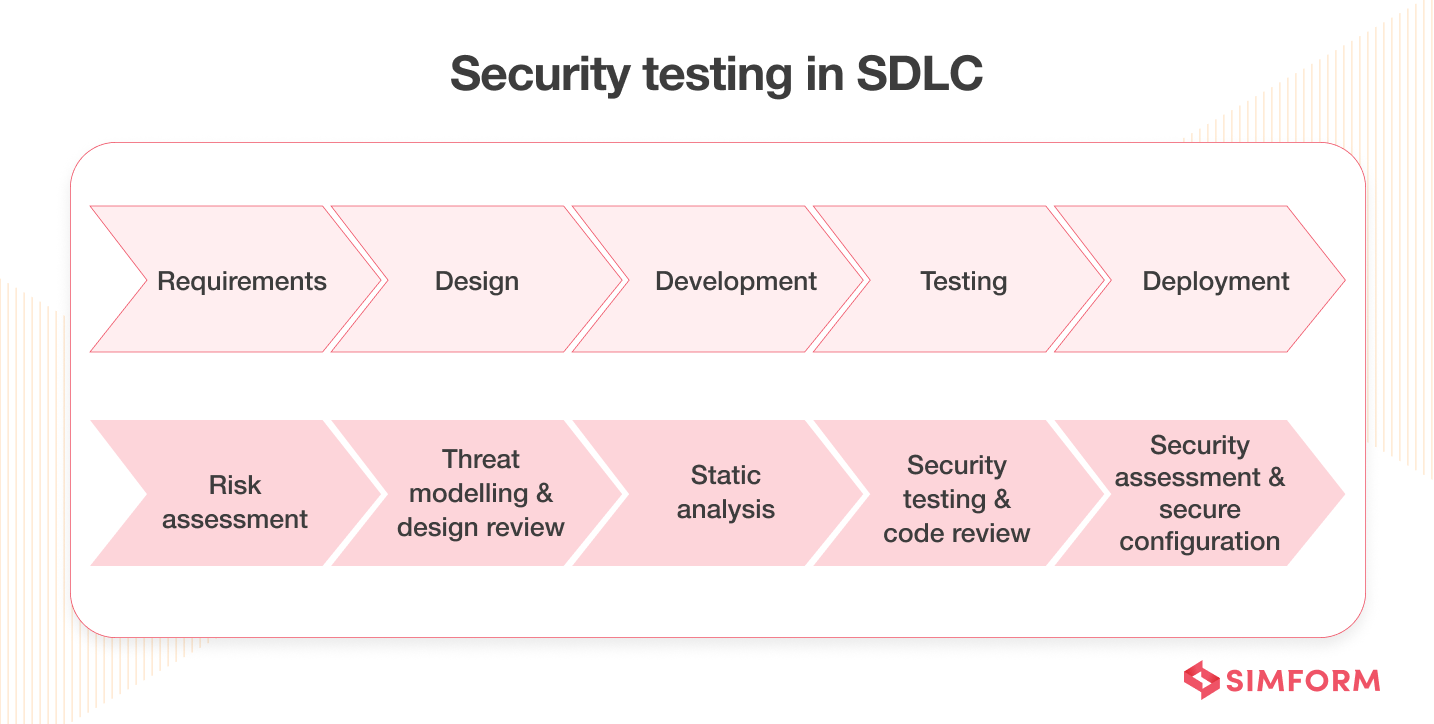
Tools like SonarQube, Intruder, Wapiti, Synk, SQLMap, Vega, etc., can help you to conduct API security testing.
It will expose the vulnerable APIs in your current application, and developers can work on it to rectify them before they become a part of a massive attack. Lastly, testing shouldn’t be a one-off process. You should perform it continuously, especially when there’s an update in the APIs.
12. Log API activities
If a security attack happens in your ecosystem, you need to find the root cause and prepare a detailed report that you can share with developers. That’s where logging comes into the picture.
If an attacker gives malicious commands to breach your security, you’ll get to know who, why, what, and when it happened. It will help you secure your APIs for the future and prevent any such attacks next time onwards.
Tools like SolarWinds, Log Analyzer, ManageEngine, EventLog Analyzer, Sematext Logs, Datadog, Site24x7, Splunk, etc., can help you log API activities.
13. Use a gateway
One of the best ways to secure an API is to put it behind a gateway. API gateway helps you to centralize your traffic and apply them to every request that hits the API. Security-related features include rate limiting, blocking malicious clients, and proper logging. Some business-related features comprise path and headers rewriting, gathering business metrics, etc.
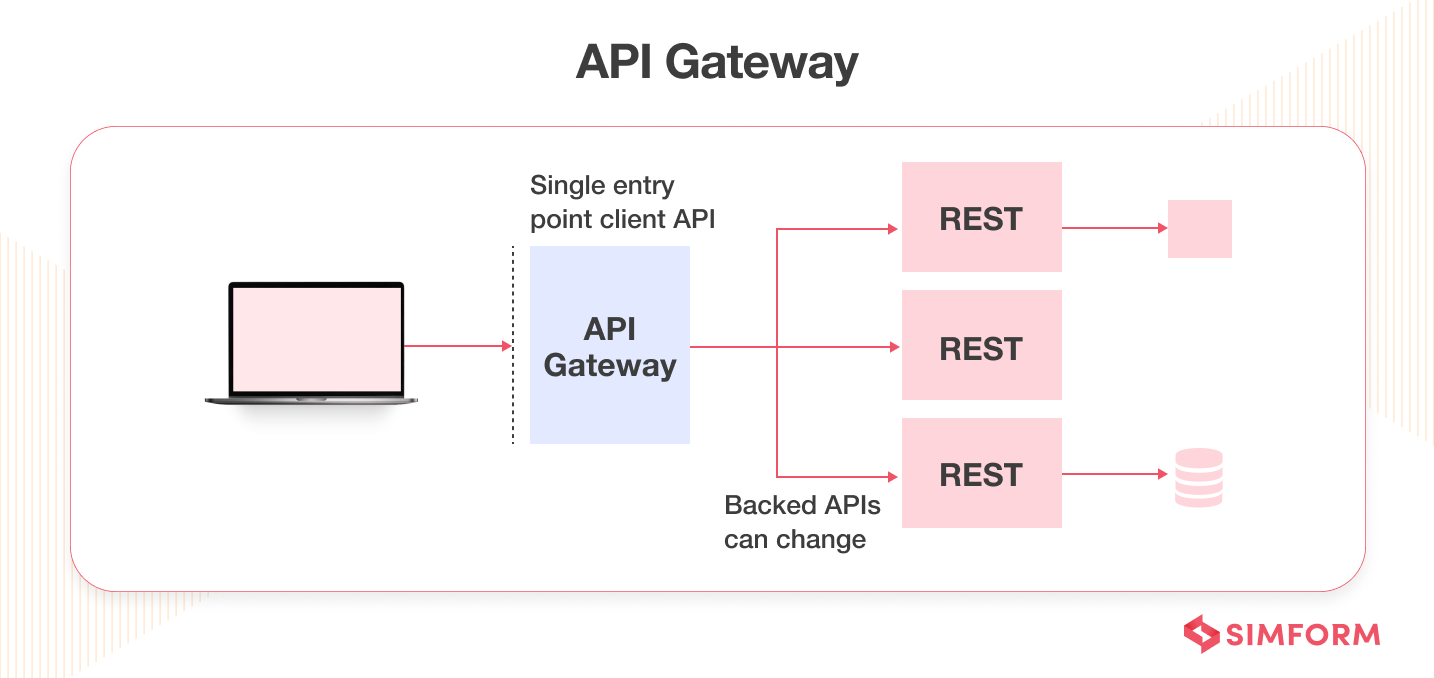
Not having these control mechanisms results in a severe security breach. API providers have to secure each endpoint individually without a gateway, which is time-consuming. Also, you can easily add or modify features with the API gateway.
14. Utilize the OAuth server
API gateways should help you to centralize the traffic. However, they shouldn’t issue access or refresh access tokens to allow malicious traffic. That task should get performed by a centralized OAuth server. Issuing a token requires operations such as authenticating the client, authenticating user accounts, authorizing the client, signing the tokens, etc.
Also, you need access to different data, such as client information or the preferred API authentication mechanisms. All these things make the task highly complicated. That’s where a centralized OAuth server is helpful. It can safely handle all these operations and reduce the burden of maintaining an API security checklist for developers. It can also control the API access. Lastly, to secure your APIs further, you can add an identity layer on top of the OAuth server.
15. Implement a zero-trust policy
In the perimeter security model, what’s “inside” the system gets trusted, and what’s “outside” the system doesn’t get trusted. However, you can’t follow such a binary when dealing with network security. A zero-trust policy must be implemented, especially with so many remote users.
The zero-trust policy is a security framework that requires all the users, whether inside or outside the organization, to get authenticated, authorized, and continuously validated for security configuration. The network can be local, in the cloud, or a combination or hybrid with resources anywhere and people working from any location.
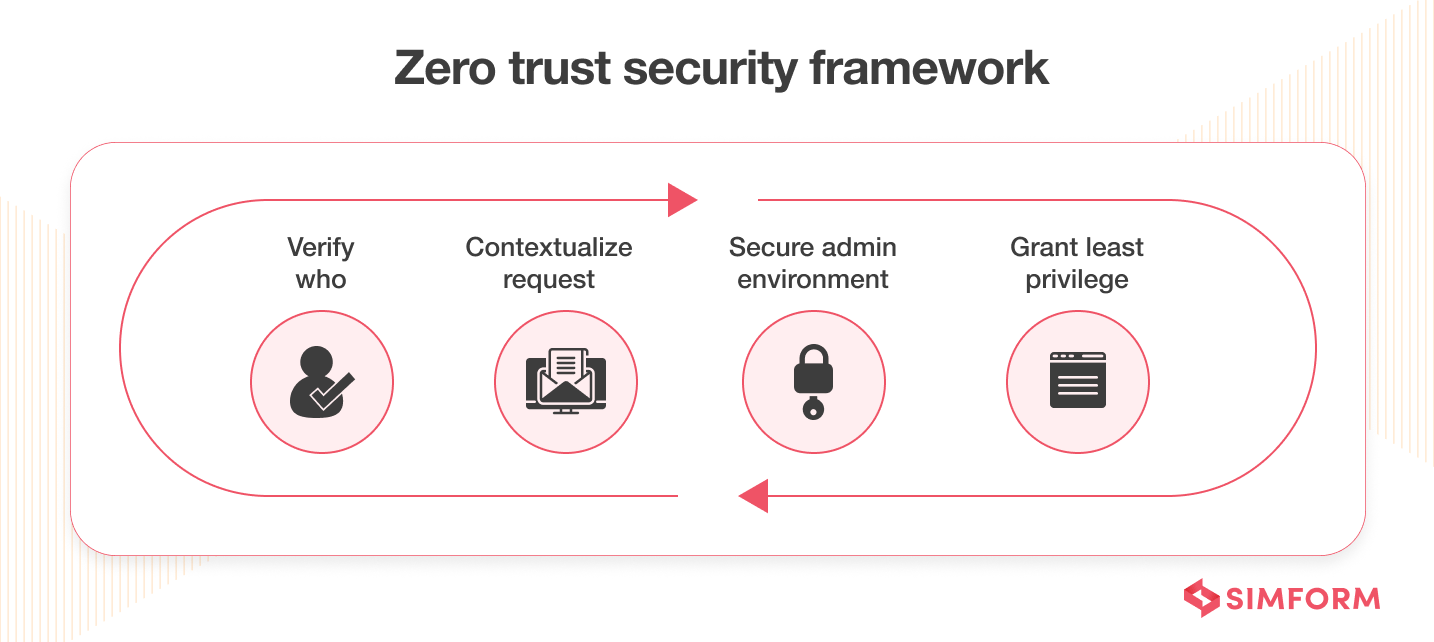
Zero-trust framework helps you to secure modern data-driven infrastructure and address the challenges of securing remote workers,multi-cloud environments, and ransomware threats. Several reputed and certified organizations enable you to implement a zero-trust policy.
16. Secure your tokens
Although tokens are not directly linked with APIs, they’re essential to securing your APIs. How securely the client handles token access management defines how secure the API will remain. If the attacker can easily stall the token, they can access the sensitive data inside APIs. Mobile and back-end apps can store these tokens securely, but developers often get challenged in web applications.
Keeping tokens secure in a browser is a dicey situation. OAuth for browser-based applications can help as it stores the tokens outside the browser, eliminating the possibility of security breaches. You can also secure your tokens with lightweight back-end components and cookie-based sessions.
17. Use a service mesh
Like API gateways, service mesh topology applies another layer of security as it helps you route requests from one server to another. A service mesh optimizes how all the system’s moving parts work together. It comprises an authentication server, data access controls, and other security measures.
Nowadays, with various companies preferring to use microservice architecture, the role of service mesh has become prominent. As the microservice scales, automation becomes essential to support that amount of APIs where service mesh can be a handful.
18. Protect your system with throttling and quotas
You should restrict the system access to limited messages per second. It will help protect your backend system bandwidth according to the web server capacity. You can also limit access through APIs to prevent unauthorized users from entering your ecosystem.
For all of this exercise, you can use throttling and quotas. It helps you prevent the system from attacks resonated from different sources with multiple requests. For example, a DDOS (Distributed Denial of Service) attack locks legitimate users out of the system. That’s where throttling can be helpful.
19. Always use TLS
Every web API should use TLS (Transport Layer Security) certificate. TLS encryption helps safeguard the secret information API sends as it only sends encrypted data when they’re in transit. You’ll know a website has TLS enabled when the URL starts with HTTPS.
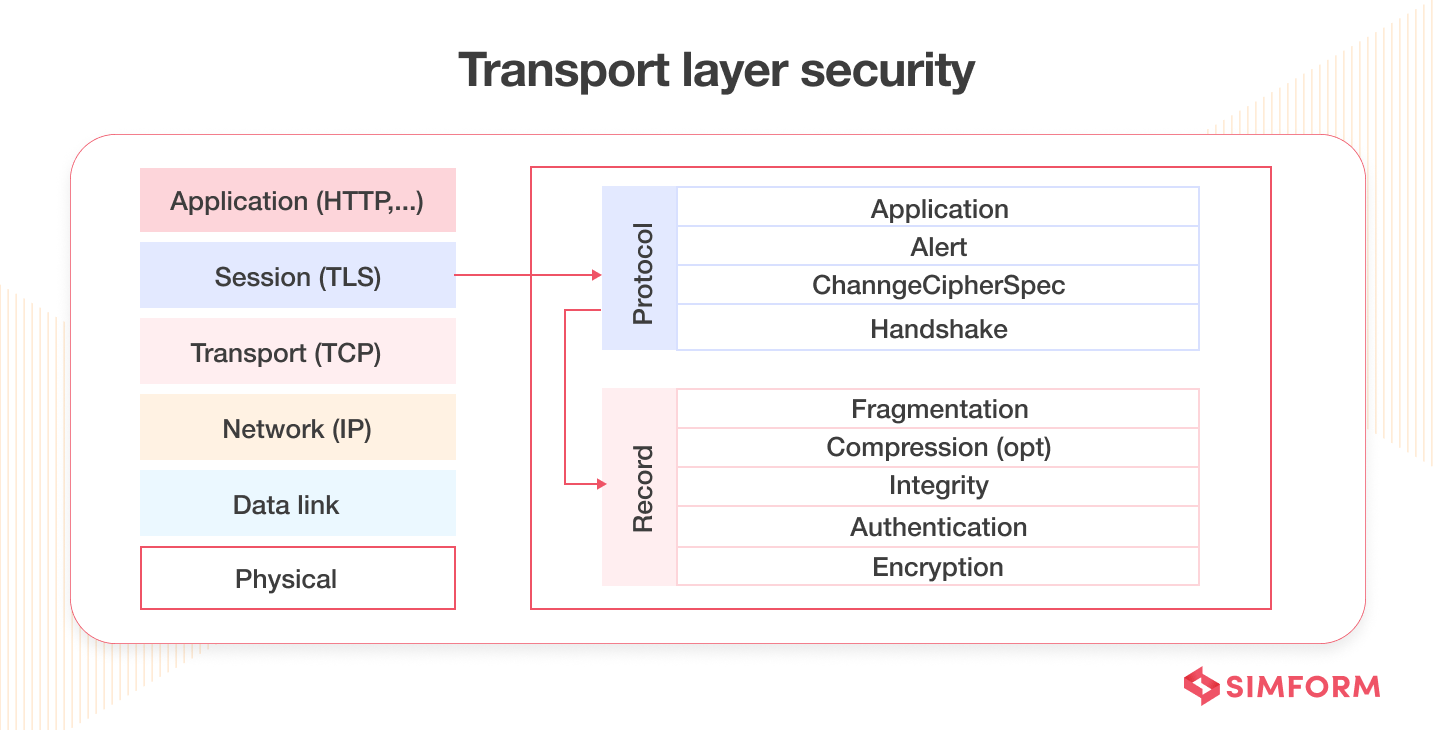
Without TLS, it’s easy for attackers to intercept the web application and read API messages that comprise sensitive information. To use TLS, you must get a certificate from the relevant authority. It lets users know that your APIs are legitimate and safe. GoDaddy, Comodo, The SSL Store, DigiCert, GeoTrust, etc., are some of the top TSL certificate providers you can opt for.
20. Understand the scope of your APIs
API security is about the APIs you develop and third-party APIs you utilize frequently. Before you build any web application comprising third-party APIs, you must understand its scope, how it works, and its associated unique vulnerabilities. Also, read the API documentation thoroughly, and analyze its process and security aspects.
One of the ways to do it is by creating a threat model. It helps you to understand the attack surface or attack vector, discover potential security issues and incorporate appropriate security best practices. Tools like Cairis, IruisRisk, Kenna.VM, Microsoft Threat Modeling Tool, OWASP Threat Dragon, etc., can help you in threat modeling.
Closing Thoughts:
In the post-covid-19 scenario, many enterprises have opted for the ‘Zero Trust‘. This is just the start – the list of cybersecurity compliance is a long, overwhelming one including GDPR, HIPAA, FISMA, CSF, PCI DSS, and NIST. So now, each security professional must bring on their A-game to safeguard their organization’s data. Please don’t hold back until it’s too late. Speak to an expert and put your mind at ease.
At Simform, we work hand-in-hand with you to develop and integrate various custom APIs and 3rd party APIs for custom software development, web apps, and mobile applications. Our API integration projects aim to save you a ton of money by reducing development time and cutting costs.
Have more questions? Get in touch with our experts