Sweet Analytics: Elevating eCommerce Marketing through Secure Data Collaboration.
Category: Advertising and marketing
Services: DevOps, cloud architecture design and review, managed engineering teams
Category: Advertising and marketing
Services: DevOps, cloud architecture design and review, managed engineering teams

Sweet Analytics is a platform for marketing and customer analytics catering to eCommerce retailers. Its services encompass an all-in-one marketing data automation tool, empowering businesses to boost sales and gain deeper insights into their customers.
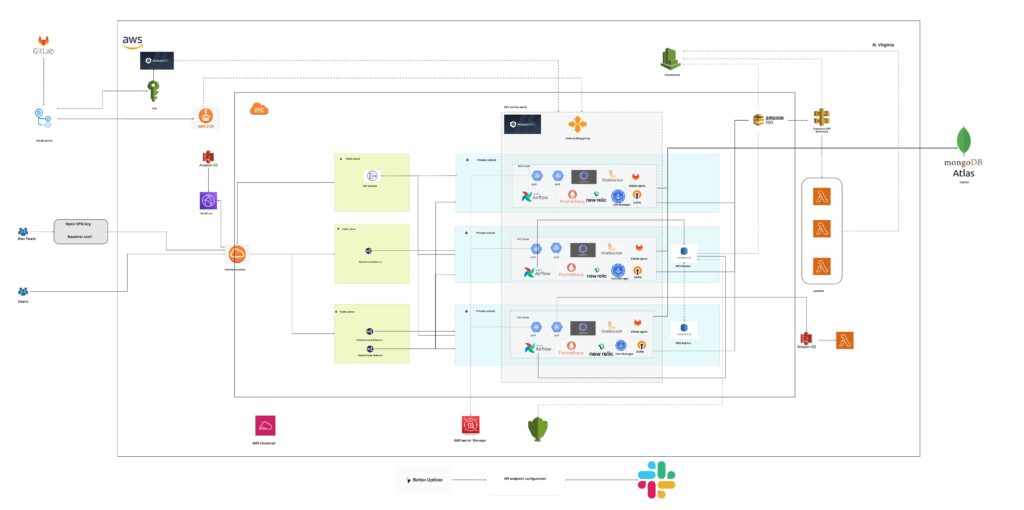
We tackled the unique challenges faced by Sweet Analytics by integrating Amazon Elastic Kubernetes Service (EKS) and employing a series of privacy-enhanced AWS and third-party services.