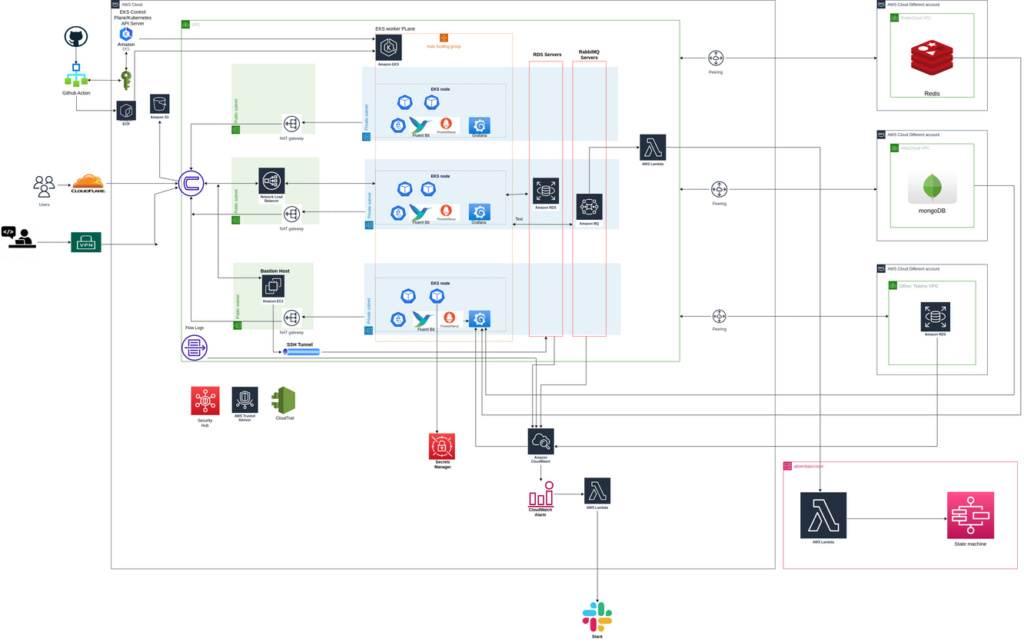
Pixis: Elevating Data Collaboration with Pixis.ai in a Privacy-Focused World
Category: Advertising and marketing
Services: DevOps, Migration, Cloud Architecture Design and Review, Managed Engineering Teams.
Category: Advertising and marketing
Services: DevOps, Migration, Cloud Architecture Design and Review, Managed Engineering Teams.

Pixis.ai is a codeless AI infrastructure company that helps brands scale all aspects of their marketing and augment their decision-making in a world of infinitely complex consumer behavior.