CarSaver: A complete one-stop solution for all your car buying requirements
Category: Automobile/SaaS
Services: Managed Engineering Teams, DevOps,Cloud Architecture Design, and
review
Category: Automobile/SaaS
Services: Managed Engineering Teams, DevOps,Cloud Architecture Design, and
review

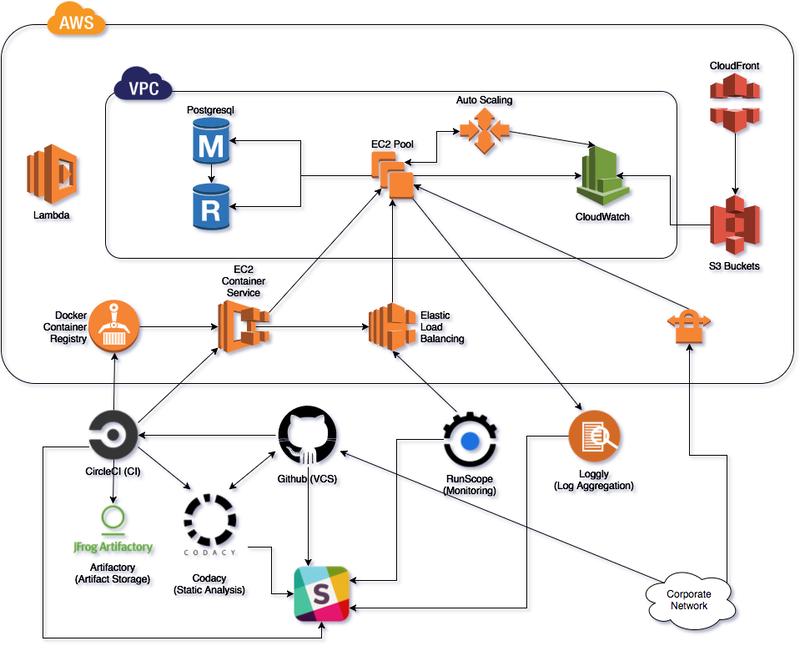
CarSaver’s platform offers an all-in-one solution for buying, renting, leasing, insuring, and upgrading cars from 30+ automobile brands, including Hyundai, Mercedes Benz, Mazda, Volvo, and Porsche. The platform is built on AWS using secure, multi-tenant infrastructure, AWS database services, and infrastructure-as-code principles to ensure regulatory compliance and simplify management for CarSaver’s customers.
Overall, our team built a reliable and secure multi-tenant solution for CarSaver to manage their customers, trades, and offers, while also ensuring compliance with regulatory requirements and industry best practices.