Picture yourself driving a car that’s past its prime. It may have served you well in the past, but today it’s outdated and unsafe. The same goes for software – as technology advances, old software becomes obsolete and insecure, putting your business at risk.
Take WinRAR for example. Its support for an outdated ACE archive format allowed attackers to extract malicious software anywhere on the hard drive, endangering over 500 million users. To tackle this issue, WinRAR dropped the support for the vulnerable format.
Upgrading to new software that’s secure, efficient, and fully supported is the solution. Of course, there may be some costs and training involved, but the risks of sticking with outdated software far outweigh the benefits.
In this blog, we’ll delve deeper into what end-of-life software means and provide guidance on how you can safeguard your business from its risks.
What does end-of-life mean for software?
End-of-life is the product life cycle stage where the vendor announces that they will not provide support for the software after a specific date. This means that the vendor will no longer release updates and security patches.
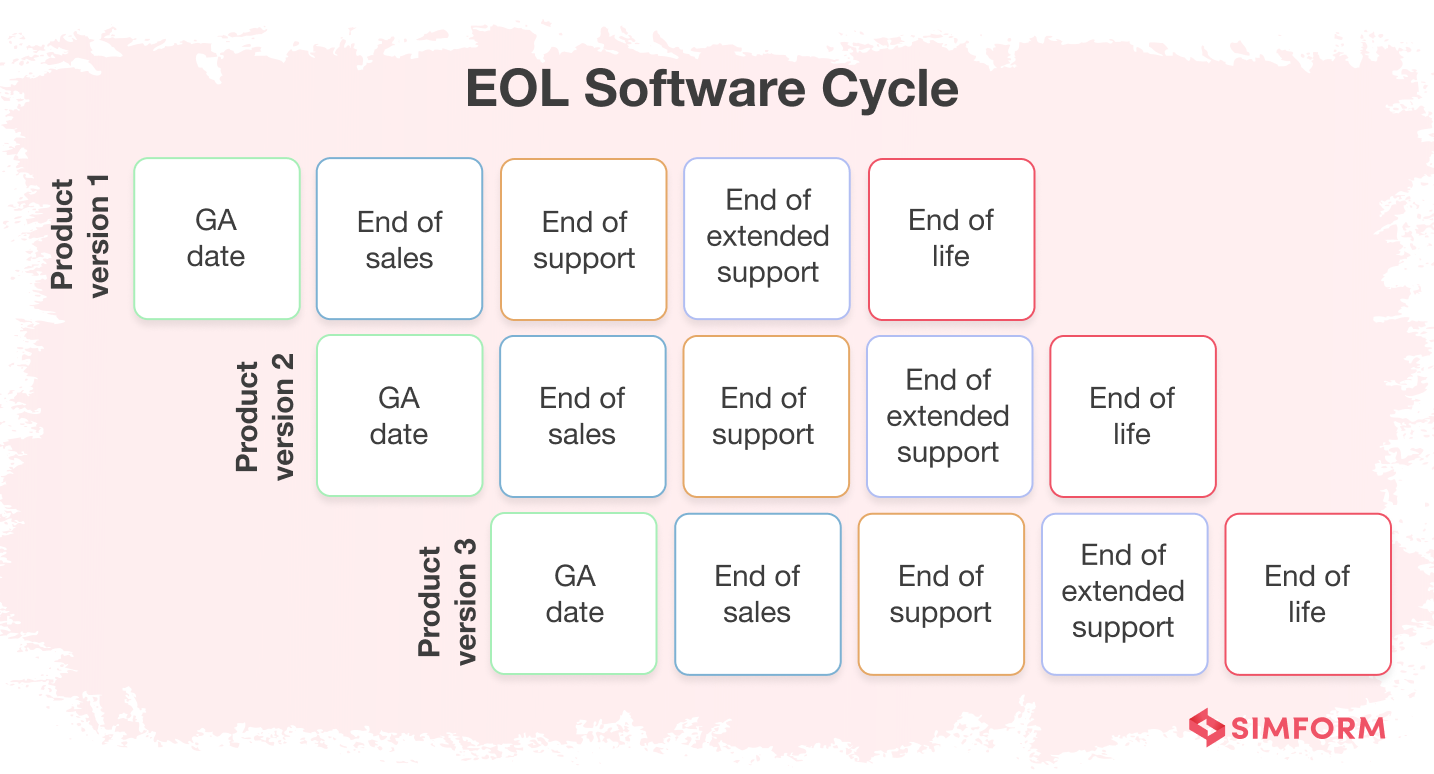
There are several reasons for this, including:
- Decision to start from scratch
- Poor product performance
- Shift in focus from outdated to recent products
What are the risks of end-of-life software?
EOL software creates vulnerabilities that hackers can exploit, leaving sensitive data and systems at risk.
Take the WannaCry attack, for example. It exploited Windows XP’s End of Life status using EternalBlue to spread malware. This led to encryption of user data and a ransom demand for bitcoin payments. Although this vulnerability was patched for newer systems, it remained exploitable after support for Windows XP ended in 2014.
WannaCry attack is just one example of EOL software risks. There are other potential risks that you should be aware of to safeguard your business:
1. Compromised security
In the case of end-of-life (EOL) programs, patches, bug fixes, and security upgrades are no longer available. As a result, your product safety is completely jeopardized.
Hacking attacks and cybersecurity incidents may put your reputation and customer loyalty at risk. Hackers may infiltrate your system, wreak havoc in the infrastructure, and compromise customer data.
Last month, Google notified its Fi cell service users of a ‘data breach’ in which hackers may have accessed limited customer information via the compromised system.
To avoid this situation, you should create a software management strategy that evaluates software regularly, upgrades or replaces EOL software, implements security controls, and trains employees to identify and report security issues.
2. Increased maintenance cost
Relying on obsolete software may cost companies a fortune. Large enterprises spend an extra cost of $4,25,000 to repair their legacy software and networks.
However, the high operating costs associated with using obsolete software are numerous:
- Support for EOL software is expensive
- The cost of additional downtime will be high as there is no technical support
- Increased labor costs due to lack of skills available
- EOL systems consume more energy than modern software, eventually increasing overhead costs
3. Lack of technical support
When software reaches its end of life, the vendor no longer provides technical support and updates. This leads to compatibility issues, and bug problems. Hence, businesses need to purchase third-party support, which can be expensive.

Apart from this, the lack of tech support poses a few more challenges:
- Slower response time
- Outdated user manuals
- Incomplete API and other documentation
- Lack of community support or forums for troubleshooting
- Lack of remote assistance or escalation process for complex problems
4. Compliance challenges
EOL software is unable to comply with industry regulations and standards like HIPAA, GDPR, PCI DSS, or SOX Act. It may also be incompatible with modern encryption standards or two-factor authentication requirements.
For example, Adobe Flash Player stopped providing support services and upgrades for the platform on December 31, 2020. As a result, organizations using Flash Player were at risk of non-compliance with GDPR.
Using end-of-life software can make organizations vulnerable to data loss and exposure, which can result in severe consequences, including hefty fines for violating GDPR.
Furthermore, the lack of audit trials in EOL software can cause compliance issues. In addition, a software vendor may fail to meet support and maintenance obligations as per contract if the software has reached its end-of-life.
5. Incompatibility with current solutions
EOL software is typically not optimized for the most recent hardware configurations. So, it becomes incompatible with the latest solutions due to updates or changes in hardware and software technology.
This lack of compatibility leads to a considerable strain on system memory and CPU. Consequently, the performance of the software can degrade, leading to slow response times, errors, and other issues.
Other than this, obsolescence of software architecture or code, dependency on outdated technology or components also results in incompatibility.
Combat EOL risks with 7 proven strategies
Creating a comprehensive EOL plan, managing inventory and supply, tracking security vulnerabilities, educating customers about the end of product life, etc., are a few ways to ensure security and stability of your systems.
Other proven strategies that you can implement include:
1. Monitor EOL status
Organizations are often caught off guard by end-of-life software. Suddenly, they find themselves without support or security updates which leads to hasty decisions that can be costly.
Knowing one’s software entails understanding what it does, its operation, and its dependencies. Understanding how to keep it running after support has ended is critical.
For this, organizations should have a plan to deal with end-of-life software. They need to consider some critical questions while planning,
- Does the product still bring adequate revenue to support maintenance costs?
- Is it relevant in the current market?
- Does the company have a better solution available?
Moreover, this plan should include identifying softwares that are at risk, .
assessing the challenges, implementing mitigation strategies, or switching to open-source alternatives.
Apart from this, organizations should pay attention to EOL emails, and proactively replace outdated software with modern alternatives. This allows them to plan and execute a smooth transition to newer products.
2. Isolate it from the network
Isolating end-of-life software protects your systems from security vulnerabilities and other risks. By restricting the access, you can reduce the surface layer of the attack, limiting the number of entry and exit points to a network or system. As a result, inbound and outbound traffic can be controlled more effectively.
Here are some ways to isolate end-of-life software:
- Identify which software needs to be isolated by checking the vendor’s website or contacting the support team
- Set up separate physical network segments or use virtual local area networks (VLAN) to isolate the end-of-life software from the main network
- Configure firewalls to block all traffic to and from the end-of-life software network segment
By isolating EOL from network, you can ensure your systems remain stable and secure.
3. Prevent the tech debt snowball
Old software or applications that are working well may not seem to require an upgrade. However, using them beyond their supported lifecycle can increase the chances of system failures and lead to higher maintenance costs, resulting in high tech debt.
In addition to this, developer shortages, inadequate quality control testing, lack of documentation, budget limitations, etc., also contribute to tech debt.
Fortunately, you can reduce tech debt by following these tips:
- Identify the most critical codebase areas that increase maintenance costs
- Improve the efficiency of the codebase by restructuring it into smaller, manageable pieces
- Invest in automated testing to make changes to the codebase without worrying about new bugs
- Replace the outdated components or libraries
- Maintain proper documentation to track real-time code changes
- Use low-code development platforms to aid developers in building complex software
4. Seek out alternative support options
Considering the fast-paced technology changes, you should prepare an action plan to reduce EOL disruptions before the product becomes obsolete.
There are several strategies that you can implement such as migrating to a supported version of the same software, or exploring alternative options that fit your requirements.
If migration is not possible, consider sandboxing or virtualization to run an application in an isolated environment with limited resources.
Another option is to go for open-source software, which provides comparable features to commercial alternatives with ongoing updates and support from a developer community.
5. Implement compatibility testing
Compatibility tests confirm the successful performance of a software application across all platforms. This will help you reduce the risk of failures and the potential embarrassment of releasing an application with compatibility bugs.
Here are the steps to perform compatibility testing:
- Define the set of environments or platforms on which the app should function
- Get well-versed with the software or application to understand its expected behavior under different configurations
- Set-up a proper testing environment by using different platforms, devices, or networks to test the compatibility of your software under different configurations
- Report any bugs you find, and fix the defects. Then, retest the fixes to confirm that the issues have been resolved
6. Consider cloud migration
Cloud migration using a software-as-a-service (SaaS) solution is an effective way to extend the software’s life and ensure continued support for the latest version.
However, migrating a huge chunk of obsolete software to a modern cloud architecture can be a costly and complicated process. To ensure a smoother migration, plan a sure-shot cloud migration strategy following the steps outlined below:
- Assess your business requirements and figure out which apps need to be moved to the cloud
- Choose a reputed cloud provider that offers services and features tailored to your business needs
- Identify and address potential issues that may arise during migration process
- Train employees on the new cloud infrastructure and tools before migration takes place
- Use monitoring tools to identify and address any issues as they arise
With a well-planned cloud migration strategy, you can ensure a smoother transition and take advantage of enhanced security, better scalability, cost savings, improved disaster recovery, increased flexibility, seamless access to modern technologies, etc.
7. Maintain consistent cybersecurity practices
To mitigate risks, you should take proactive measures to identify potential flaws in your organization’s IT policies.
First, assess your existing IT policies to determine if it covers software disposal strategies. Secondly, ensure that sensitive data files are securely removed from the system, and stored and transmitted using encryption.
To strengthen cybersecurity, its important to follow policies related to password strength and changing passwords. Additionally, compliance with regulations like National Defense Authorization Act or Payment Card Industry Data Security Standard is also crucial.
Modernize your applications for a better tomorrow
Once your software has reached its EOL stage, there’s no bulletproof way to keep it operating. The potential risks of security, compatibility and compliance typically outweigh the rewards, especially if you’re on a shoestring development budget.
The solution is to modernize your software through strategic planning and lifecycle management.
By modernizing older apps with newer approaches to computing, you can improve efficiency, security, and structural integrity. And the best part? You don’t have to figure it out on your own.
Here’s our detailed guide on how to effectively modernize EOL software for a better tomorrow. Don’t let outdated software hold you back, modernize today!